Identify, Extract and Publish Encrypted Session Metadata
The Containerized Visibility FabricSM (CVF) cloud native network function for encrypted session visibility is powerful capability to see and manage encrypted session traffic.
Encrypted Session Visibility
CVF agents provide the ability to identify, extract and publish all the encrypted session parameters and data that providers need to support all their cryptographic visibility, management and security demands. Regardless if it is to identify, monitor or quantify encrypted exchanges or to ensure the reliability and stability of systems, to differentiate legitimate cryptographic exchanges from potentially malicious unknown, unreliable or questionable traffic. The CVF architecture publishes all the metadata and traffic of interest needed to support analytics, decryption, storage and forensic analysis services.
Encrypted Session Processing
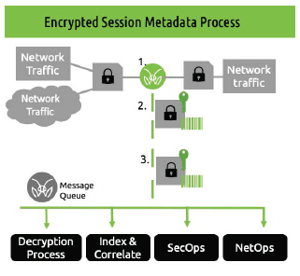 1. Agents monitor, identify and access encrypted session controls and associated traffic
1. Agents monitor, identify and access encrypted session controls and associated traffic2. Agents selectively extract and publish any or all of the following:
- Encrypted session metadata
- Encrypted session key metadata
- Encrypted session plain text
3. Follow on processing. The specific encrypted session controls and/or associated traffic of interest are used by subscriber programs to support an/or enrich a broad range of event correlation, decryption management, topology mapping, storage, or forensic analytics applications.
The MantisNet CVF performs a variety of complex functions for monitoring cryptographic controls, anywhere in the infrastructure. This cloud native, composable solution goes beyond capturing packets to publishing new forms of encrypted session metadata to enable cryptographic monitoring and follow-on processing.
The CVF architecture is an innovative combination of network sensor agents, and cloud native technologies that efficiently produces all the information necessary to monitor the cryptographic status and health of your infrastructure as well as feed follow-on analytic solutions for decryption management and forensic analysis.
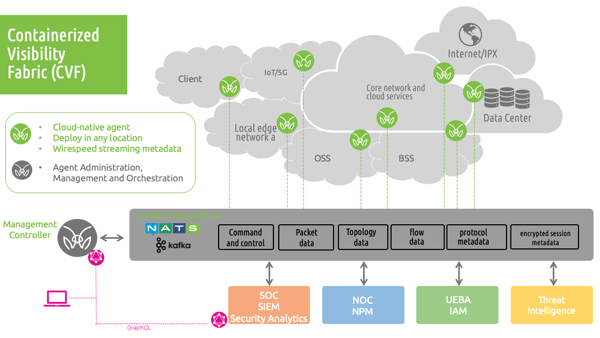
Learn more about the containerized visibility fabric.