Introduction
In the security industry, visibility is everything. As the old adage goes, you can’t stop what you can’t see. This is why Palo Alto Networks created the Next Generation Firewall and why Mantisnet is seeing such incredible traction with its cloud-native tools in order to fully instrument control, management and dataplane messaging/traffic at the kernel level. When Palo Alto Networks was created, most firewalls were “stateful firewalls”, and policies were created based on a “5-tuple”, where the 5-tuple was the source and destination address and port, and the protocol (TCP or UDP). What happens though when you have multiple applications running on the same port? How do you stop bittorrent on port 443, but allow HTTPS traffic to legitimate web sites? Thus was born the Next Generation Firewall that could secure any application regardless of what port or protocol it was running on.
As we look to 5G networks, especially those in an enterprise environment, the need for this sort of visibility has only increased. In enterprise 5G networks, not only do we have various applications running, but we have various device types on the network as well as a new entity not normally seen in an enterprise environment, a 5G Core (5GC). The 5GC Network Functions (NFs) communicate with each other over protocols like HTTP2, PFCP and GTP. These protocols and interfaces must be secured or the security of the 5GC and the Enterprise is at stake. To properly secure these NFs and their interfaces, security sensors must be able to decode these protocols and in many cases, offer stateful correlation between traffic on various interfaces and NFs.
5G Network Visibility and Zero Trust
As industry leaders in network visibility, Palo Alto Networks and Mantisnet are perfectly situated to provide the sort of intelligence and insight into network behavior and security needed to secure an Enterprise or even Government 5G deployment. Gone are the days of perimeter security, instead a new approach of Zero Trust security is needed to continuously verify each flow from each element on the network. Only with a Zero Trust security posture can enterprises know that the appropriate applications are being accessed by the appropriate users and that traffic is free of Threats. Palo Alto Networks offers numerous tools to provide a Zero Trust architecture, but today this blog will talk about a specific one that is a new twist on an old approach.
N6 Security - The Old Way
Mobile network operators (MNOs) have for years deployed a form of security where perimeter firewalls on their mobile network would allow almost all outbound traffic from devices and block almost all unsolicited inbound traffic from the rest of the world (primarily the internet). This approach has been in place for 3G, 4G and now 5G networks. The name for this firewall was derived from the 3GPP interface it sat on. In 3G networks it was on the “Gi” interface, so it was called a Gi Firewall, on 4G networks it was on the SGi interface, so it was called an SGi Firewall, and in 5G, they decided to go with a totally new interface name, and since the firewall resides on the N6 interface, you guessed it, its called an N6 Firewall.
Historically all of these Firewalls have looked at traffic only up to layer 4 of the OSI Model (e.g. the 5-Tuples discussed above). This means that these firewalls were typically unaware of the applications, the content, or the devices sending and receiving the traffic. With this lack of visibility it is impossible for a legacy N6 Firewall to offer Zero Trust security, which is a requirement for Enterprise 5G networks.
N6 Security - The Right Way
An overhaul is needed for the N6 Firewall, especially when deployed in enterprise environments. Instead of being a firewall that is based on ports and protocols, it needs to be application aware. Furthermore, it needs to be able to look inside the payload of the traffic and identify malware, URLs, Domain Names and Exploit attempts. This sort of visibility has been supported by the Palo Alto Networks NGFW for years now and is leveraged by thousands of enterprise customers already. The question is, how do we take those capabilities and use them in a 5G network?
Before we answer that, we have to talk briefly about Zero Trust security postures, and what they entail. This blog won’t go into much detail on Zero Trust, you can read more here. In short, to offer a Zero Trust security posture, you must eliminate implicit trust, and answer the following questions below for each flow, as defined by the Kipling Method:
- Who should be accessing a resource? This defines the asserted (e.g. 5G) identity
- What application is the asserted identity of the packet using to access a resource inside the protect surface?
- When is the asserted identity trying to access the resource?
- Where is the packet destination?
- Why is this packet trying to access this resource within the protect surface? This relates to data classification, where metadata automatically ingested from data classification tools helps make your policy more granular.
- How is the asserted identity of a packet accessing the protect surface via a specific application?
Today this blog will focus on the first bullet, the “Who” of each flow. Ideally for a Firewall on N6, after the Firewall has identified all the other parameters (what, when, where, etc.), it would also answer, “who”. But this is a non-trivial question to answer, especially for a Firewall sitting on N6. The Palo Alto Networks NGFW can answer this question of “who” easily when it is on other 5GC interfaces, but on N6 it needs additional input. This is where the visibility offered by Mantisnet comes in.
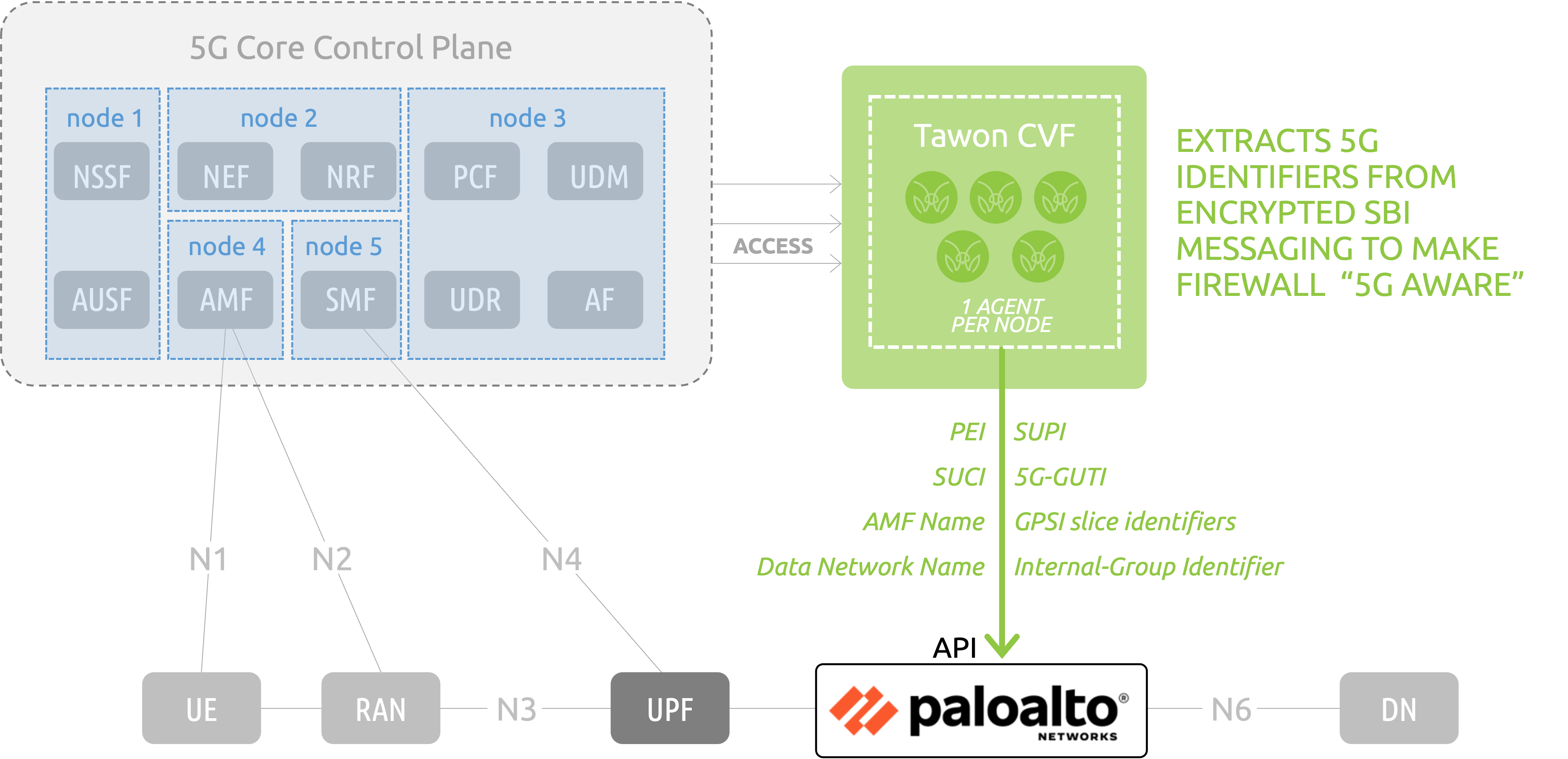
MantisNet's Tawon CVF is a cloud-native, Containerized Visibility Fabric (CVF) for extracting virtual resource data from distributed computing environments. Tawon CVF was designed, from concept, to handle the challenges of gaining deep visibility into virtualized environments where topology, interfaces, processes, and data flows are hidden and increasingly ephemeral.
Leveraging a lightweight microservices framework and eBPF technology, Tawon CVF can be deployed quickly, at-scale, to provide federated, “dynamic resource” characterization. Extended Berkeley Packet Filter (eBPF) functions constitute a relatively new and powerful set of capabilities embedded in the Linux kernel. eBPF “event-handlers” enable a variety of important use-cases in modern cloud-native environments. Use-cases span across application and network performance monitoring, service mesh, load balancing, continuous discovery, dynamic topology and anomaly detection for a variety of development, systems engineering, operations, cloud infrastructure, 5G / IoT, and cybersecurity applications.
The MantisNet Tawon Containerized Visibility Fabric (CVF) is equally adept at monitoring encrypted traffic and cryptographic controls, anywhere in the infrastructure. This cloud-native, composable solution goes beyond capturing packets to extracting, processing and publishing new forms of encrypted session metadata to enable comprehensive cryptographic monitoring and supporting streaming analytic (AI & ML) workflows follow-on processing to bring clarity to obscured network functions.
Tawon CVF has solved the encryption problem for the majority of environments, enabling visibility into plaintext (unencrypted) traffic in those cloud native environments. Tawon CVF supports a simpler, faster, more efficient way to access and inspect encrypted traffic and plaintext directly with a container-native agent co-residing in the cloud infrastructure where the encrypted traffic is generated and consumed providing access to the following types of metadata:
- Encrypted session messaging - client/server hello exchanges
- Encrypted session plaintext - providing plaintext prior to or post- encryption processes
- Encrypted traffic - for follow on decryption or forensic inspection
In the example illustrated below, Tawon is tasked to instrument the messages associated with Control Plane SBI activity on an Open5GS/UERANSIM testbed, extract the relevant 5G identifiers (3GPP, Informational Elements) and push the identifiers to the Palo Alto Networks NGFW via API to extend the N6 NGFW functionality to become 5G “aware”.
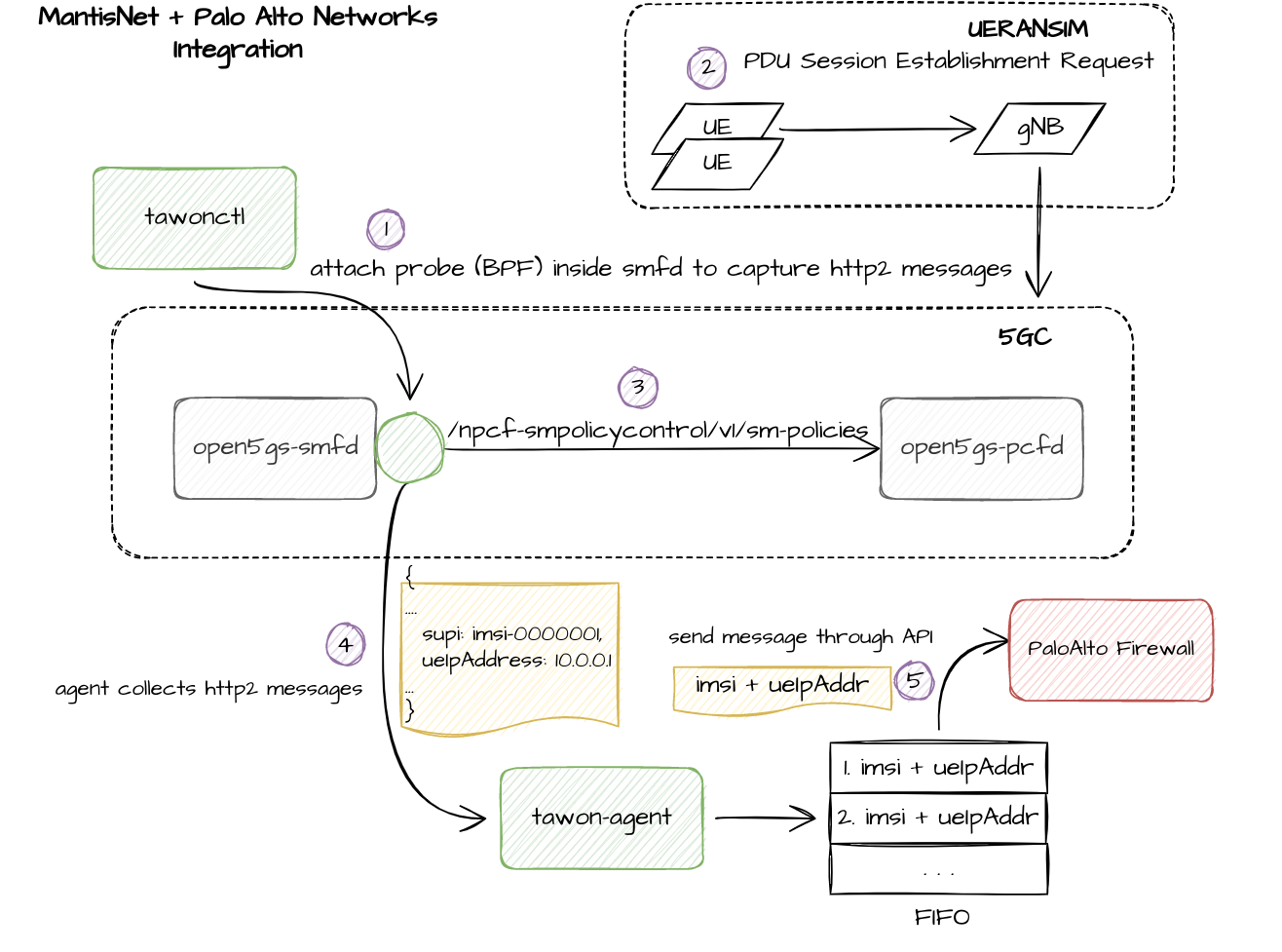
MantisNet-Tawon learns the Subscriber and Equipment IDs of users as they attach to the network and leverage APIs on the NGFW to push this metadata to the NGFW. In the example below, we leveraged the User-ID API to push the mapping of IMSI-to-IP address to the NGFW. For instance, if a user attached to the network and received an IP address of 10.45.0.2 from the 5GC, the mapping of that IP address to its IMSI would be pushed from Mantisnet to the NGFW. This accomplishes two important things.
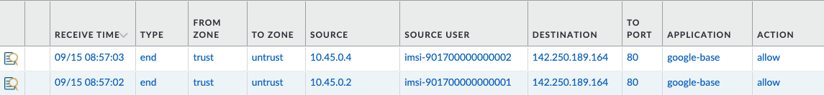
- The NGFW now shows the IMSI for this user in all logs, including Traffic, Threat, URL and Wildfire logs. This means if there is malicious traffic from this user (or towards this user), the SOC will receive more than just the IP address, it will also receive the Subscriber information, so it instantly knows the affected user/device.
- This visibility allows the enterprise to enact security policies based on the Subscriber identity. This means if a certain set of users are allowed access to a resource, but another set is not, policies can be created based on the subscriber IDs (IMSIs) to enforce this security posture. IP addresses of the device can change, but the policies will remain effective.
Below is an example of a traffic log showing the user's IMSI in the User-ID field.
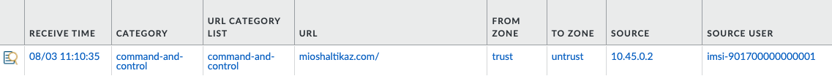
Similarly, when threat traffic is observed, the Threat/URL log will also contain the User. In the example below we attempted to browse to a Command and Control server over HTTP, and had our traffic blocked. Because the User is shown in the log, the SOC, SOAR systems, etc. which receive these alerts can take timely action.
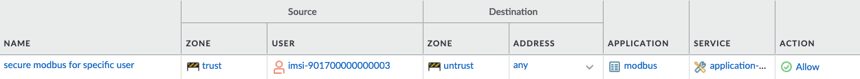
Finally, using the User-ID value, enterprises can create policies specific to the users and devices on their network. In the policy below we allow modbus traffic for a particular IMSI.
Summary
Visibility is everything when it comes to effective security. As this joint solution has demonstrated, coupling two cloud native technologies from Palo Alto Networks and Mantisnet gives customers deploying 4G and 5G networks the ability to have both visibility, and the security that comes along with the Palo Alto Networks NGFW and the Mantisnet Tawon solutions. But why take our word for it? Let us show it to you on your own private mobile network. To quote yet another adage, seeing is believing.


