Where cyber criminals previously bought credentials and account information on the black market, they are now more likely to use sophisticated forms of exfiltration malware to automate the credential stealing process to get access to vast amounts of even more valuable information.
These tools give attackers the ability to collect, exfiltrate, and exploit thousands of stolen credentials using secure (encrypted) communication channels within a short amount of time.
So, how do you know when attackers are attempting to steal credentials and how do you stop them? What's the answer?
Credential Stuffing and ATO Help Increase Financial Gain for Attackers
Cyber-crime is a global business. Attackers are in the business of infiltrating your systems for their own monetary gain. It has been widely reported that automated credential-stuffing attacks make up to 90% of login traffic on internet-facing systems. Some attacks are state-sponsored, and others are corporate espionage, but organized cyber criminals are definitely in it for the massive amount of data and the resulting revenue that can be had by selling information on darknet markets.
Unfortunately, widely available forms of sophisticated malware tools, as well as poorly protected and exposed systems, enable many attackers to quickly grow from small-time cyber criminals to a global enterprise-level hacking professional.
1. Attackers typically begin by using phishing emails, trojans, compromised websites, previously infected hardware ( i.e., thumb drives or IoT appliances), or wireless hotspots and access points to distribute exfiltration malware on a massive scale.
2. Once the victim's system has been compromised with malware, and the malware has been activated, it then performs any number of operations such as memory-scraping, cross-site scripting, and key logging to scan files for account logins, credentials, passwords, and PII. The malware then (or already has) initiates a secure connection with the attacker's system or command and control server (C&C) to automatically initiate the exfiltration of the data.
* Account Takeover Tools (ATOs) automate the login process using credential stuffing, which is a subset form of brute force attacks. Brute force attacks using scripts are not a new form of cyber-crime, but ATOs make it much more challenging to detect and give the attacker the ability to run thousands of login attempts across the web, unlike traditional scripts. ATOs make credential stuffing attacks more efficient and provides widespread access to multiple services using victim credentials. Attackers can verify credentials, steal data from the victim's account, initiate transfers, or order products using the victim's account information.
3. Now the attacker has tens of thousands of usernames, passwords, and credit card numbers that he intends to use to target his intended victim's sites. The attacker then validates the stolen credentials of the targeted enterprise(s) by attempting to log into the system or, in the case of an e-commerce site, buy low-cost items.
4. Once the attacker has tested the credit card purchases on store applications, he now has a list of validated credit cards and credentials that can be used for bigger purchases either at the same store or on a different site. In most cases, this doesn't affect the retail system, but it does cost money in chargebacks, shipped products, and user complaints.
Monetary gain isn't always in the form of credit card theft and purchases. Attackers can cash out using indirect methods such as reward points. Sites that store what seems like innocuous information are often much more poorly secured. In 2014, hackers uploaded millions of Hilton Rewards member account numbers from compromised accounts to forums and other darknet markets. Attackers were able to gain access to credentials from poorly secured authorization methods on the Hilton website. Legitimate users could log in using a username and password or a member number and 4-digit PIN. Using phishing and brute force, attackers gained access to these accounts and emptied millions of dollars in cash rewards from them.
Alternatively, criminals are increasingly targeting trade secrets and proprietary business information for rapid financial gain.
The opportunities are endless, but examples include business plans, internal financial reports, chemical or pharmaceutical formulas, manufacturing processes, product designs, geological data, copyrighted content, and software. Recent examples include very sophisticated organizations such as Lockheed Martin with the theft of the F-36 Joint Strike Fighter designs to the computer and network security company RSA where criminals stole information related to the company's SecurID two-factor authentication technology; as well as consumer product companies such as Sony and Coca-Cola where attackers used spear-phishing tactics to exploit systems, upload keyloggers, and steal passwords to gain access to business plans and proprietary information.
In all of these examples, attackers were successful in obtaining copious amounts of compromised account credentials. Going through each record one-by-one would take too long, and the organizations would have been alerted before they could go through all of the accounts. Instead, they use automated ATO tools to log in and cash out. With ATO tools, an attacker can log into the system and break into or steal from thousands of accounts in a short amount of time before the business detects an issue. These tools are also used to discover credential reuse across multiple applications on different sites.
So, once again we are left with the question, "What is the answer?"
Using PPEs for Defense against ATO and Credential Stuffing
A Programmable Packet Engine is the answer. The PPE is an in-memory compute engine that can be configured to continuously monitor network traffic, initialization protocols, and log-in attempts to detect attacks in real-time as they occur. The PPE detects, identifies, and allows you to stop credential/account takeover attacks in real-time by detecting and identifying the unique "fingerprint" of the operations performed by the malware in the initial handshake exchange between the victim's system and the attackers command and control C&C server in real-time - BEFORE stolen information can be exfiltrated in encrypted form.
This is done by looking at the initial exchange between the victim's system and the attacker's systems, specifically the SSL hello headers. By installing the PPE, either as a network appliance on your network or as a containerized service running in your cloud or virtualized environment, you can continuously and silently read, detect, and block credential theft and ATO activity in real-time.
When a client computer connects to a web server, it first sends initial SSL packets called the handshake. SSL data is encrypted, but the initial "hello" record contains information about the client such as the SSL/TLS protocol version, a session ID (empty if it's the initial hello packet), and the cipher suite supported by the client. A PPE monitors the physical network interface on the server, so it can detect the client software used to create an SSL/TLS connection request.
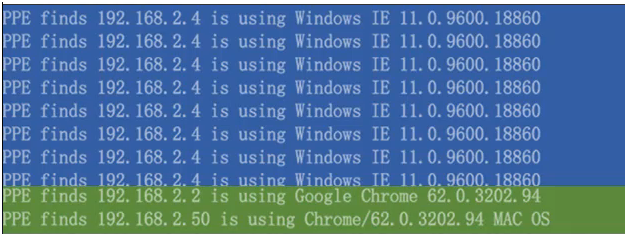 PPE detecting client software used to connect to the server
PPE detecting client software used to connect to the server
All credential stuffing malware / ATOs have unique characteristics of the information exchanged during the hello request; this is referred to as their fingerprints, and this information can be used to identify and block the connection.
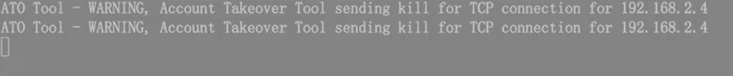 PPE detecting an ATO
PPE detecting an ATO
The PPE does this by comparing the SSL hello packet fingerprint with a database of thousands of fingerprints from known Account Takeover Tools. The PPE can also be used to identify and monitor seemingly legitimate TLS/SSL exchanges in order to identify suspicious new types, or zero-day, attacks. Once known bad/malicious connection attempts are detected, the PPE can facilitate sending a TCP kill message to the server, which responds by removing the connection from the malicious attacker while leaving your legitimate connections intact.
PPE Benefits
The benefit of the PPE is that it can be installed as a real-time network monitoring appliance, or as a small, lightweight application running in your virtualized environment; it continuously detects malicious activities in real-time, and interfaces with your existing security infrastructures (such as threat/intrusion detection/prevention and data loss protection systems...) to identify, block, isolate, or terminate the responsible applications or systems. It provides a level of continuous and real-time security unparalleled in the cyber security space. Not only can the PPE identify and help stop malicious activity, but it can also save businesses from intellectual property theft, regulatory penalties, chargebacks, reputational damage, and financial losses.
Want to see the PPE in action?



