This technique takes enterprise web filtering a step further from standard cyber security systems (IDS/IPS and SIEM) software and supports a broader integration with multiple analyst tools to better identify malicious sites on-the-fly, rather than leaving your network security exposed to outdated databases or questionable data sources.
The tool that is used to accomplish this? MantisNet's Programmable Packet Engine (PPE).
Deriving Intelligence from DNS Metadata
Before getting into how you can analyze DNS traffic, the first step is to place a virtual or physical TAP (test access point) on the network that will then send a copy of the information to a PPE. The insertion of the TAP allows the PPE to analyze real-time network traffic information by network protocols, as opposed to relying on post-event, log-based reporting mechanisms.
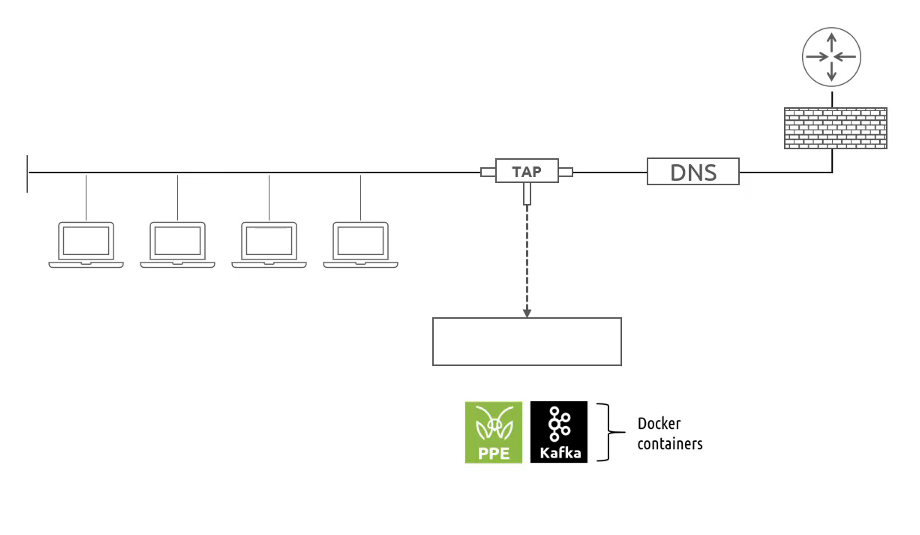 Typical network topology with a TAP and PPE installed
Typical network topology with a TAP and PPE installed
Notice in the above diagram that the lightweight PPE and the Apache Kafka streaming platform are installed via Docker containers. These containers are deployed within a server, forming a MantisNet sensor. The sensor is what alerts the SOC (Security Operations Center) Analyst of sites that could host malware of suspicious content.
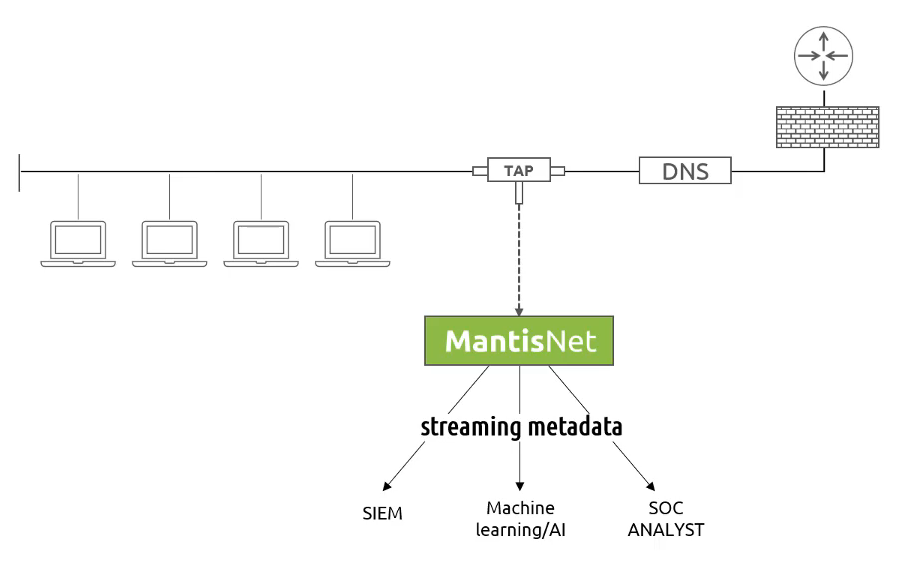 Typical network topology with a MantisNet sensor
Typical network topology with a MantisNet sensor
Using Kafka, the MantisNet sensor can continuously stream metadata to multiple locations in real-time, but for this article, we will focus on the SOC Analyst. The stream is formatted in JSON, so that you could send this data to any tool or auditing software with JSON parsing capabilities. Since JSON is a well understood data interchanging format, the sensor can be used with most of the current generation of IDS/IPS, SIEM or threat detection platforms that offers intelligent cyber security analytics.
The SOC Analyst could have any number of tools to help automate alerts, but the primary goal for an analyst is to watch network traffic and perform continuous real-time "background checks" on suspicious domains. With hundreds or thousands of users on the network, this can be overwhelming. Instead of watching all traffic manually, a set of metrics can be used to alert the Analyst of a suspicious domain DNS lookup for further review.
Any DNS lookup tool can be used, but for this example, we used six common metrics to determine the safety of a domain:
- ISP owner
- Domain age
- Alexa 1M status
- Dynamic domain (Y/N)
- Domain length
- Top level domain check (TLD or ccTLD) (i.e., .cn or .ru)
If any of these metrics return an alert, a tab is opened on the Analyst's browser for further review.
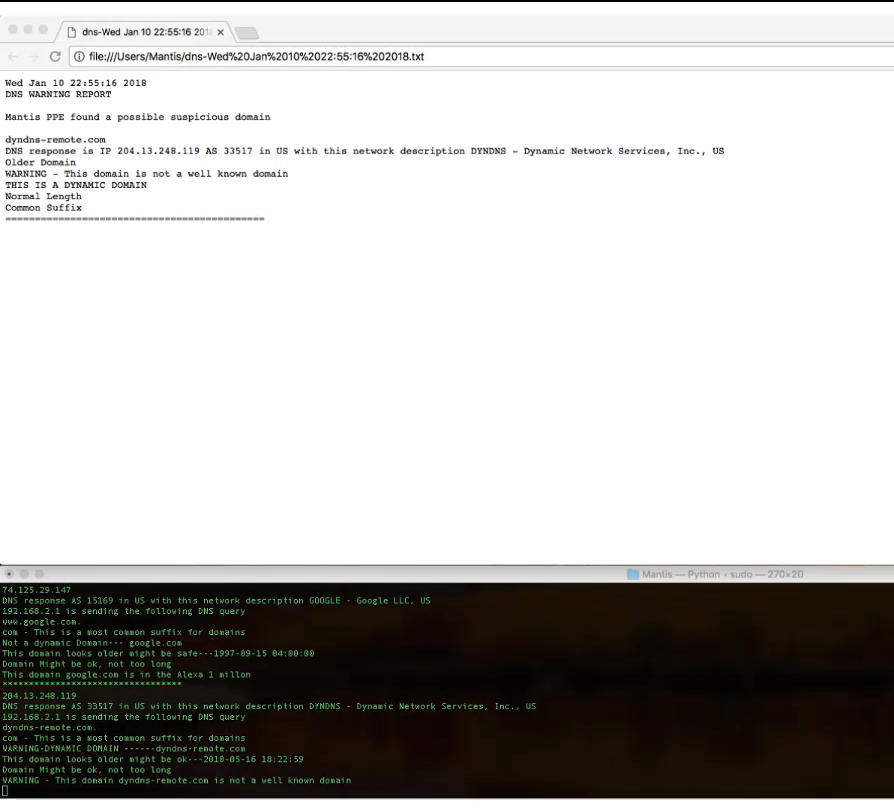 PPE alert of a suspicious domain
PPE alert of a suspicious domain
From this view, the Analyst can use his own tools, as well as any number of third-party, or open-source sites on the web. Two open-source tools available to anyone are VirusTotal and Google's Transparency Report.
Let's use a dynamic DNS domain that might be flagged as suspicious from the PPE. The PPE automatically opens two open-source tools for the Analyst to review. The first -- VirusTotal -- shows server headers and some basic information about the domain.
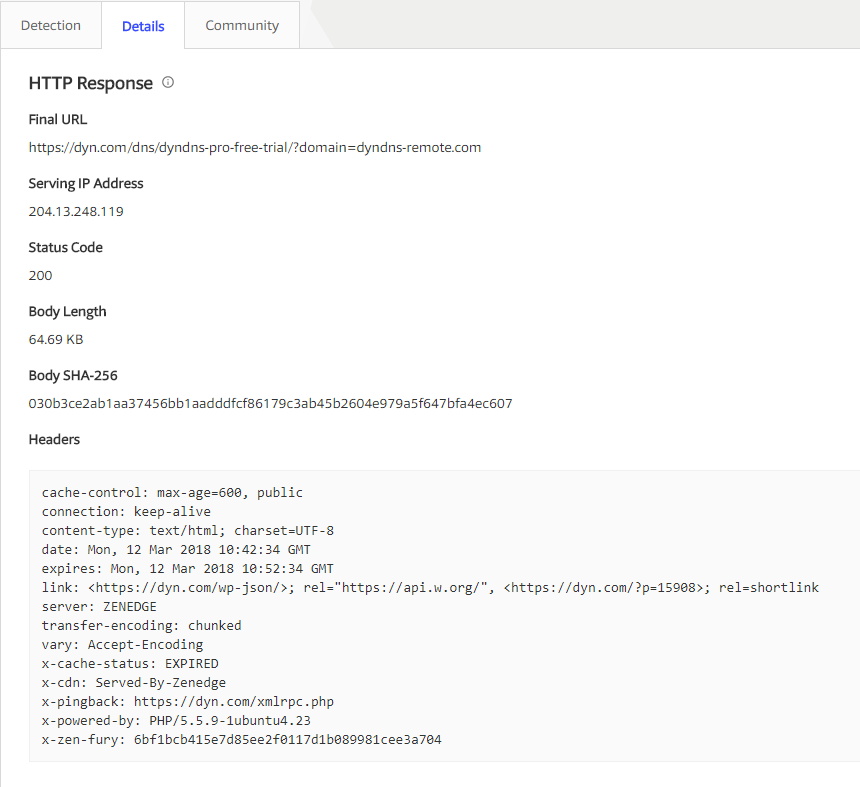
VirusTotal report
A Google Transparency report also opens that gives the Analyst a background on the host's AS (autonomous system) network. With Google Transparency, if a large percentage of malware sites are hosted on the same AS, the host is flagged as a possible malware threat.
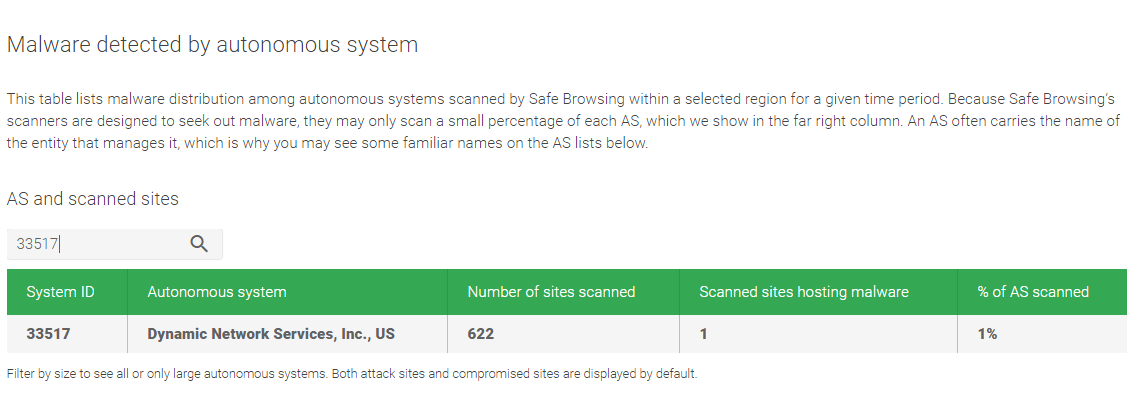
Google Transparency Report
These are just two examples of open-source tools that can be used as preliminary background checks. Additionally, there is a wide variety of more sophisticated, commercially available, security and threat analytics software that can ingest PPE generated metadata. Some examples include:
- SIEM: Splunk, Elastic, LogRhythm...
- Orchestration Software: Cyberbit, Phantom, CyberSophos...
- Endpoint Software: Tanium, Carbon Black, Sophos...
- CTIs: Proofpoint, FireEye, CrowdStrike...
- TIPs: Anomali, ThreatConnect, ThreatQuotient...
Continuous DNS Monitoring with the PPE
It is important to emphasize that the metadata produced by the MantisNet sensor is a continuous view of what is occurring on the network, formatted in JSON. The metadata is a "real-time building block" which the SOC Analyst can send to multiple tools already at their disposal.
With the PPE, SOC Analysts now have the ability to access data in real-time as well as augment existing tools (which often rely on analytics of static or stale log data) with real-time, streaming network information - dramatically increasing the accuracy and reducing TTI (time to identification) and TTC (time to containment) of DNS-based attacks.
Utilize Real-Time Monitoring to Protect Your Network
Utilizing the PPE, you can identify and stop threats by better understanding the communications taking place between network devices and related network protocols taking place on your network and alert your own security team should communications be made with any known bad or suspicious domains. As a result, your users are prevented from rendering content in their browsers that could be malicious, malware downloads are blocked, and serious cyber security threats can be prevented before they reach your network.
Want to see the PPE in action?
Don't hesitate to Contact Us with any questions, or visit the PPE FAQ page.



