The recently announced NSA "instructions for National Security System (NSS), Department of Defense (DoD) and Defense Industrial Base (DIB) system administrators on how to detect, prioritize and replace unauthorized or deprecated TLS protocols with ones that meet current standards.”
Encrypting communications is one of the most critical tools for protecting data. However, if older and out-of-date encryption protocols are in use, that presents a vulnerability that could be exploited to gain access to systems or networks. Updating to the latest TLS 1.3 and the heavily supported TLS 1.2 along with compliant cipher suites and strong authentication is recommended.
As per the guidance, “Previously, the National Security Agency previously released urgent guidance (ORN U/OO/800922-17) indicating that obsolete  and otherwise weak TLS protocol implementations were being observed, and threat intelligence stating that “nation-state and sufficiently resourced (read: criminal) actors are able to exploit these weak communications.”
and otherwise weak TLS protocol implementations were being observed, and threat intelligence stating that “nation-state and sufficiently resourced (read: criminal) actors are able to exploit these weak communications.”
The accompanying Cybersecurity Information Sheet, “Eliminating Obsolete Transport Layer Security (TLS) Protocol Configurations” (PDF) provides instructions for system administrators as to how to detect, prioritize, and replace unauthorized or deprecated TLS protocols with ones that meet current standards. Notably, the first step is to detect obsolete TLS protocol implementations in use. This is done by both following the proscriptive guidance contained in the document, combined with cybersecurity best-practices and active defensive measures, specifically monitoring network / cloud traffic flows to identify the sources of obsolete TLS configurations in the environment. Additionally, the NIST 800 -53 and other standards that leverage the framework require continuous monitoring for potential vulnerabilities and active exploitation.
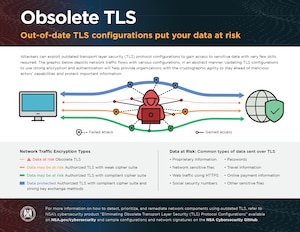
As this relates to MantisNet CVF customers, they can extract and publish encrypted session metadata to identify deprecated forms of Transport Layer Security (TLS) or Secure Sockets Layer (SSL) for traffic sessions at risk of sensitive data exposure and decryption. MantisNet CVF metadata contains specific details of the TLS encrypted session version, the cipher suites in-use as well as the application/process/flow level details are then extracted to support correlation, analysis and remediation of the exchange in question.
Please prioritize the monitoring for out-of-date encryption protocols to reduce your risk. To speak with one of our engineers on this topic, contact us.



