Peter Dougherty
Peter Dougherty, CISSP, is a technology entrepreneur, strategist & operating executive with over 25 years of experience developing and delivering cyber security, networking, compute, and storage technologies.
The Time is Now For (MantisNet) 5G Observability
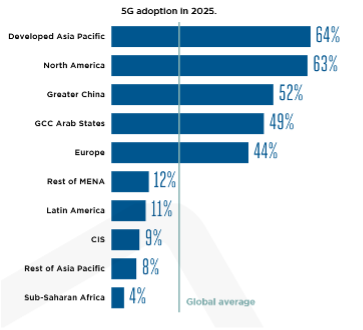
Forecasts through 2025 Show a 3x Increase in Global 5G Adoption, with 85% of Global Carrier Capex Spending Earmarked for 5G
According to recent market data from GSMA Intelligence (www.gsmaintelligence.com/) the tipping point for the global transition to 5G applications has been reached. As a result, the roll-out of 5G deployments is poised to dramatically accelerate over the next three years. In confirmation of these predictions, we’ve also seen numerous recent announcements about the acceleration of coverage and the 5G subscriber growth from carriers and service providers around the world around (see AT&T, Vodafone, Telefonica, and Deutsche Telekom).
Read More
Today’s cloud-native systems are built using containerized, distributed micro-services-based architectures. Accordingly, the Application Programming Interfaces (APIs) these systems utilize are the key to understanding the operations, status, and communications within those systems. Consequently, having deep API-Centric visibility is both critical and necessary for operations and security.
Read More
What is eBPF, and why is it so important?
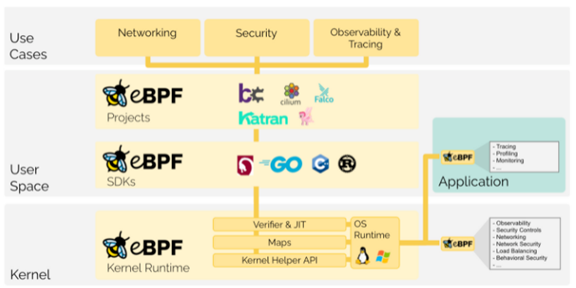
The Extended Berkeley Packet Filter (eBPF) functions constitute a relatively new and powerful set of capabilities embedded in the Linux kernel. First released in 2014 (w/ Linux 3.18) we are seeing accelerating adoption of eBPF for very good reason.
The access that eBPF provides enables a variety of important use-cases in modern cloud-native environments. Use-cases span across application and network performance monitoring, service mesh, load balancing, continuous discovery, dynamic topology and anomaly detection for a variety of development, systems engineering, operations, cloud infrastructure, 5G / IoT, and cybersecurity applications. We discuss these in more detail further below.
Read More
Tags:
network engineering,
network preformance,
Real-Time Monitoring,
mantis,
containers,
5G
The recently announced NSA "instructions for National Security System (NSS), Department of Defense (DoD) and Defense Industrial Base (DIB) system administrators on how to detect, prioritize and replace unauthorized or deprecated TLS protocols with ones that meet current standards.”
Encrypting communications is one of the most critical tools for protecting data. However, if older and out-of-date encryption protocols are in use, that presents a vulnerability that could be exploited to gain access to systems or networks. Updating to the latest TLS 1.3 and the heavily supported TLS 1.2 along with compliant cipher suites and strong authentication is recommended.
Read More
Tags:
cyber security,
Real-Time Monitoring,
mantis,
cybersecurity
As another year is completed, now is the time to spend reflecting on the state of technology, cybersecurity and innovations. The year 2020 (and previous years) has revealed some uncomfortable truths, despite our best efforts towards improving the future prospects for clients and our industry. We are confronted with some key issues to take to heart, to improve on what has been brought to light through recent cyber events – including the Marriott, TikTok, & Solarwinds incidents - among the growing list of breaches.
Read More
Tags:
cyber security,
mantis,
containers
The 5G era is here. Soon carriers will begin offering 5G services to enable many new and exciting applications for this technology. The consumer applications for 5G are numerous; gaming, autonomous vehicles, video, commerce, tech-enabled medicine, retail, finance coupled with AI, ML, and AR/VR: all of these will provide a new level of user/customer experiences. This will be achieved by an ecosystem of telecommunications infrastructure, software and service providers in support of both existing and new forms of carriers and operators. The White House published the National Strategy to Secure 5G earlier this year and it is worth the time to read it in its entirety.
The ecosystem of players are working hard to define and build a resilient 5G infrastructure that meets the new speed and scale requirements, while also adopting new and open technologies that disaggregate hardware and software functions.
Read More
Tags:
mantis
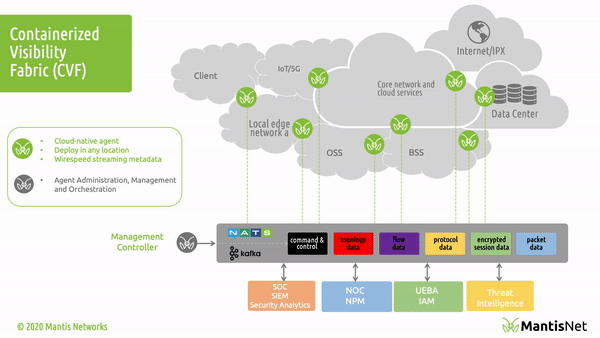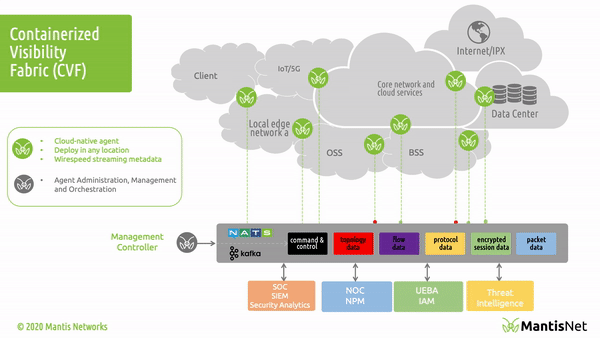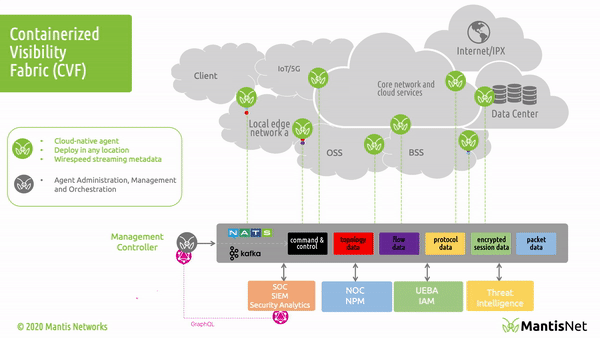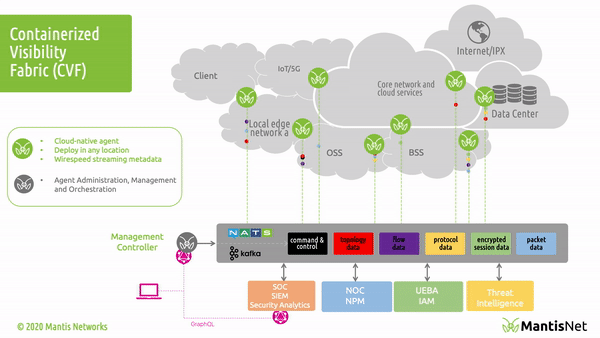
In our last post “Introducing the MantisNet CVF: Solving Cloud Native, Serverless, Observability Challenges“ we provided an overview of the Containerized Visibility Fabric (CVF) capabilities and made some assertions about how revolutionary and disruptive cloud-native technologies are, the resulting opacity problems, as well the art of the possible insofar as enabling next-generation observability.
In this installment we’ll go into more detail as to what exactly we mean by cloud-native observability as well as the significance, deeper implications of it, interoperability and investment protection. So, let’s revisit containerization, and by extension, why cloud-native observability is so revolutionary.
Read More
Tags:
Real-Time Monitoring,
Data-In-Motion,
mantis,
cybersecurity,
containers,
cloud native network function
The MantisNet Containerized Visibility Fabric (CVF) is now generally available, and we want to provide a deeper dive into the challenges that we’ve seen with network visibility which compelled us to develop this much needed cloud native observability solution.
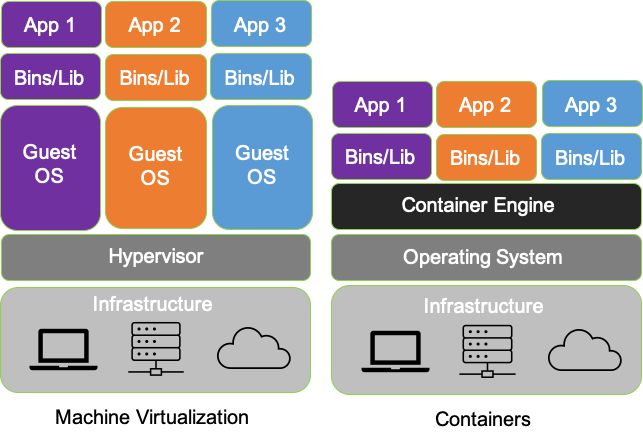
As we will discuss more deeply in this and future posts; serverless, cloud native systems are unique in that applications are deployed as microservices and containerized applications which can both more fully exploit the capabilities of the underlying machines and are further decoupled from the constraints of hypervisors. This provides programmatic visibility and access to the underlying nodes (hardware - machines) in such a way as to enable better scaling, fault isolation, observability and control.
In the cloud native world; network topology (physical and virtual) is hidden, interfaces (network namespaces) are hidden, data flows are hidden, and to make matters even more challenging - resources are dynamically configured, provisioned, deployed and reused.
Read More
Tags:
Real-Time Monitoring,
mantis,
containers,
cloud native network function
As we’ve shared previously - networks are the circulatory and nervous systems of your enterprise. Indeed; “the network is the computer”, and networks are an invaluable source of ground-truth. From a communications perspective, you can learn a lot by directly observing who is speaking, to whom they are speaking, the language they are using, the tone of voice, and the content of the communications. When it comes to network communications and metadata the analogies are obvious: in the case of DNS traffic- mapping URLs into IP addresses, and identifying underlying services and connected devices - in the case of TLS protocol, getting detailed insights into the encryption capabilities and device characteristics - likewise the GTP protocol provides geo-location specific information, and in the case of the MODBUS protocol, understanding the communications within industrial control systems.
Read More
Tags:
Real-Time Monitoring,
Data-In-Motion,
mantis,
cybersecurity
DNS. A necessary mechanism that makes global network communications work, connecting services to the internet or private network, thereby powering our digital lives can also present confounding and problematic engineering challenges with cybersecurity implications. Site not responding, nefarious applications, applications not resolving, broken network connectivity…many initial responses are Is it DNS? it’s DNS, “It’s always DNS”.
DNS, the domain name system, connects domain names to IP addresses that locate and route information and traffic from a source location to a client can be the bane of many network and cybersecurity engineers as they maintain networks or investigate potential threats on the network.
We’ll look at this critical network component, its threat value and how you can make DNS an actionable component
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis,
cybersecurity