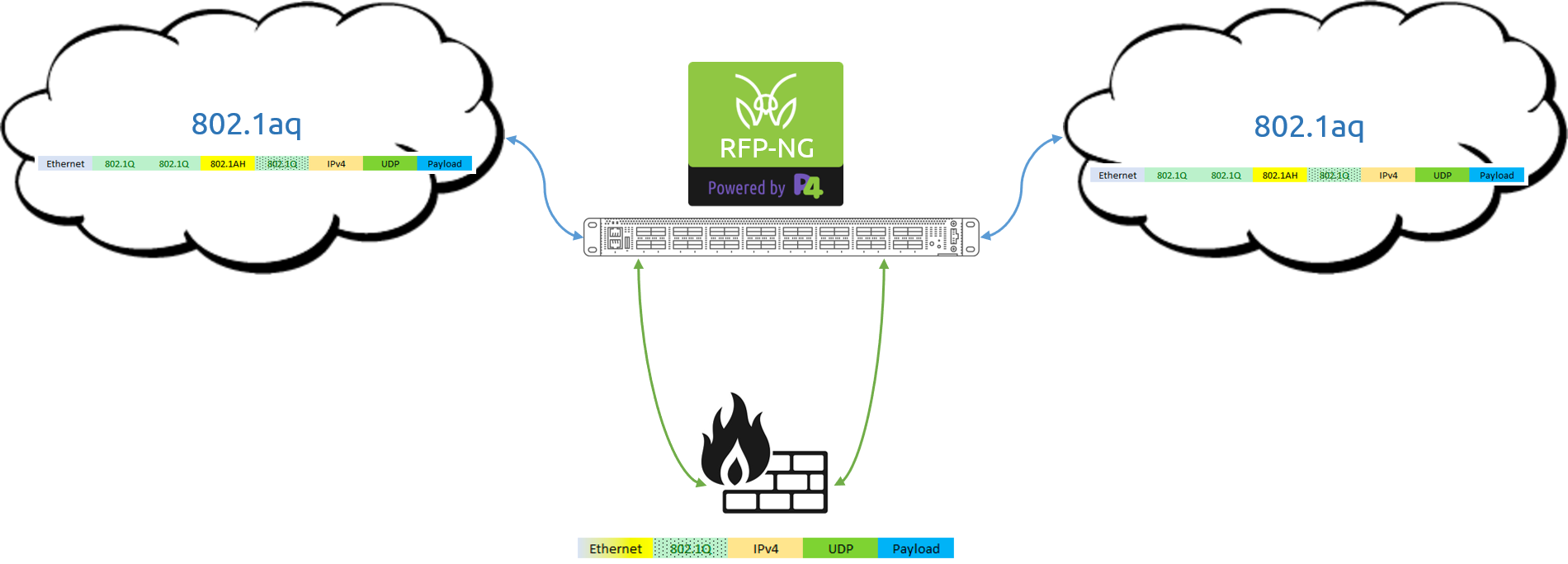
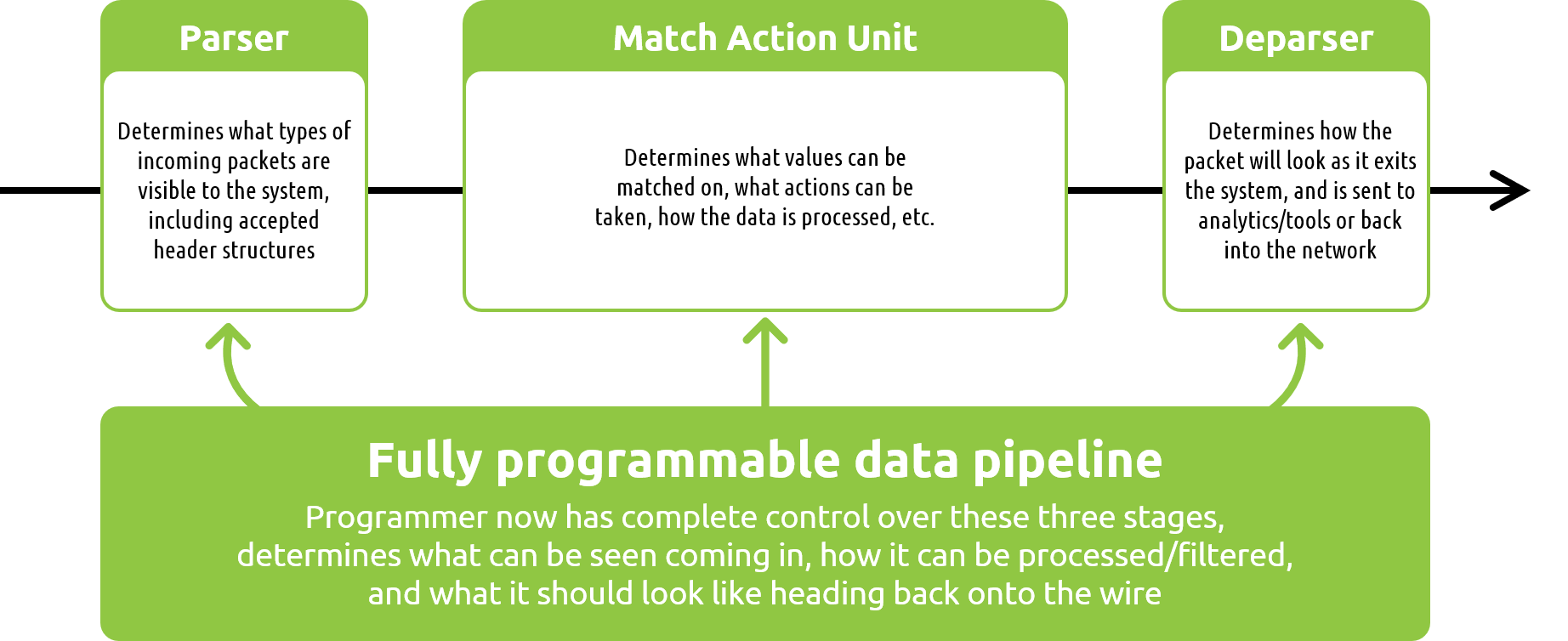
This is a continuation of our blog series on the advanced functions for network visibility solutions with fully programmable data pipelines. Read our introduction to the series here.
The biggest elephant in the network visibility room has always been the fact that you don’t know what you are missing. If there are packets with structures that fall outside of your fixed-function ASIC-based chip/solutions capabilities (and trust me, there always are), you are not only going to drop those packets, but you also have zero indication that you just missed a packet. The packets simply fail to parse, and you will not know that you are missing that information. You can’t control, what you can’t see.