One of the biggest drivers that has impacted the design of 5G systems is the goal of providing extremely low latency and high-speed data rates throughout the entire network. The increase in data delivery speeds with 5G environments promises staggering benefits- we are talking about moving from the 1 Gbps world of 4G into a promised 10 Gbps future- or more simply put, an evolution akin to shifting from the horse and buggy to internal combustion engines. Such an enormous jump in the speed at which the world’s most valuable resource (data) can be exchanged helps explain the amount of energy and excitement around 5G that we are all collectively experiencing.
But how does this translate into architecture principles?
Leaving carrier aggregation (CA) and massive MIMO aside for another conversation, we will focus on the network itself. For starters, the 3GPP determined early on that the control plane (CP) and user plane (UP) must be split (across both the RAN and the core) so that each plane can be independently scaled and flexibly deployed. In addition to this split, the decision to take a NFV/SDN, or “cloud-native” approach to the underlying resources is critical in achieving the promised speeds of 5G. Cloud-native allows for centralization of compute resources, and optimization of all physical resources that are serving network functions (NF), regardless of location in the network.
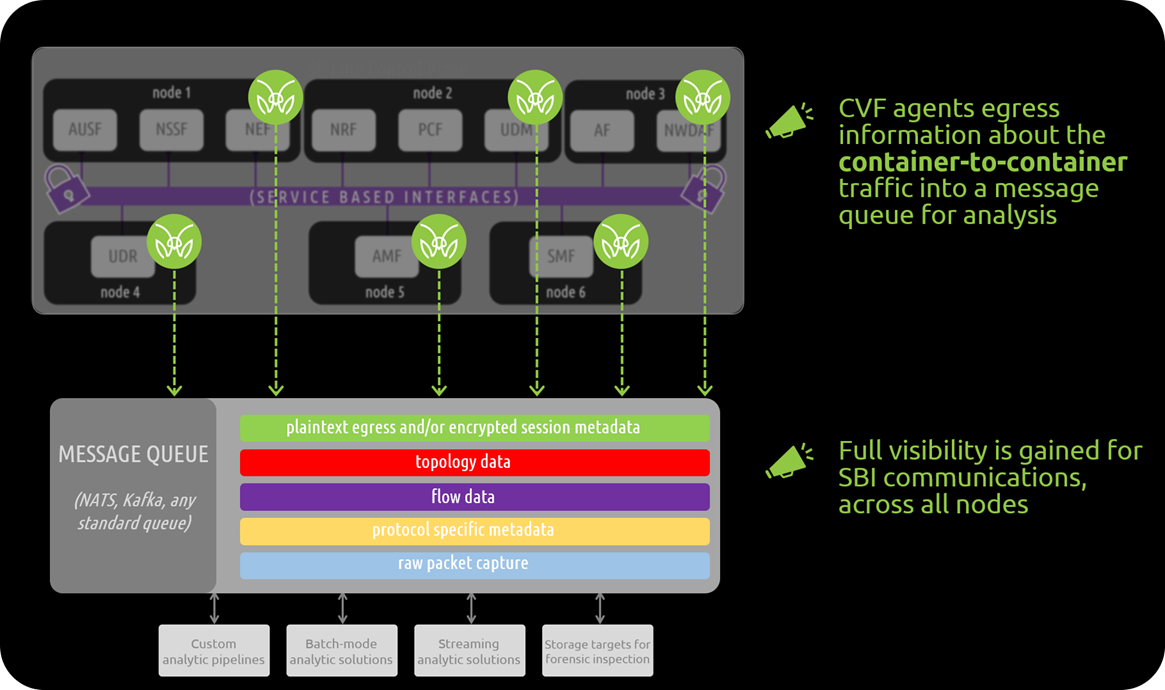
NF communications within the SBA