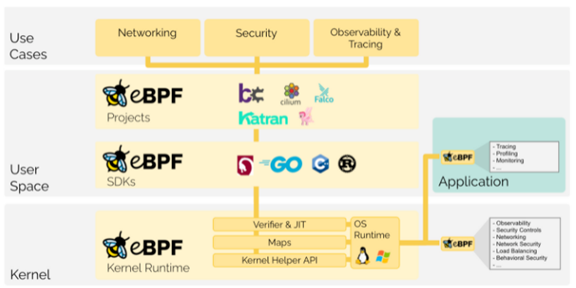
What is eBPF, and why is it so important?
The Extended Berkeley Packet Filter (eBPF) functions constitute a relatively new and powerful set of capabilities embedded in the Linux kernel. First released in 2014 (w/ Linux 3.18) we are seeing accelerating adoption of eBPF for very good reason.
The access that eBPF provides enables a variety of important use-cases in modern cloud-native environments. Use-cases span across application and network performance monitoring, service mesh, load balancing, continuous discovery, dynamic topology and anomaly detection for a variety of development, systems engineering, operations, cloud infrastructure, 5G / IoT, and cybersecurity applications. We discuss these in more detail further below.
Read More
Tags:
network engineering,
network preformance,
Real-Time Monitoring,
mantis,
containers,
5G
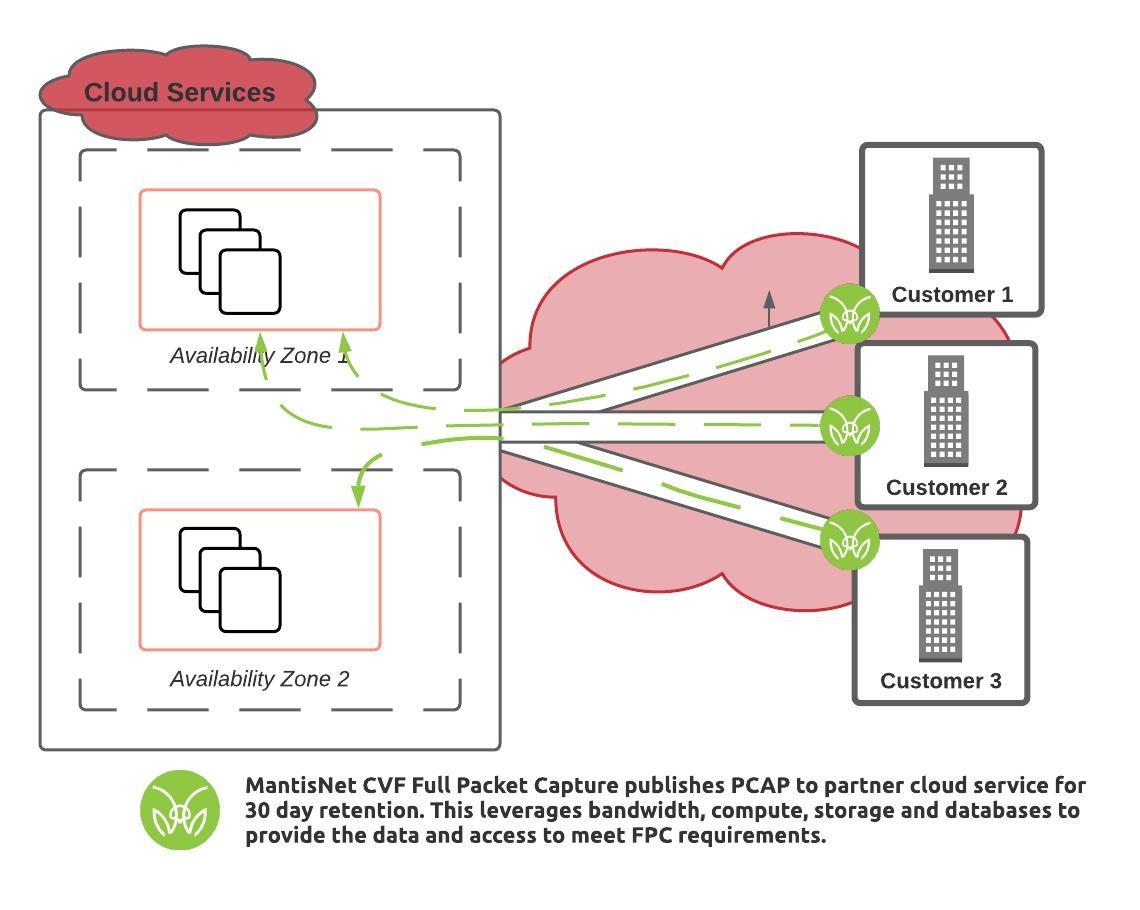
How a cloud native packet capture platform can meet the DoD SCCA Requirement
Traditionally full packet capture systems exist to obtain the network communications between various hardware devices – servers, switches, routers – in a physical network environment. With the advent of Kubernetes and cloud native environments that type of traditional approach is no longer effective (or relevant) to provide information into ephemeral resources. Information from microservices and containers such as pod-to-pod, namespaces, and intra-pod communications, etc. are critical for continuous observability and forensic inspection for performance, security, and reliability engineering applications. The evolution of infrastructure and network communications has evolved into virtualized and cloud native architectures such that new technologies are needed to operate and monitor those systems.
Recently, we were approached to partner with a global cloud service provider (CSP) to meet the Department of Defense Secure Cloud Computing Architecture Functional Requirements PDF (DoD SCCA) for Full Packet Capture (FPC) by providing a cloud native FPC solution for their new environments.
Read More
Tags:
network preformance,
cyber security,
mantis,
containers
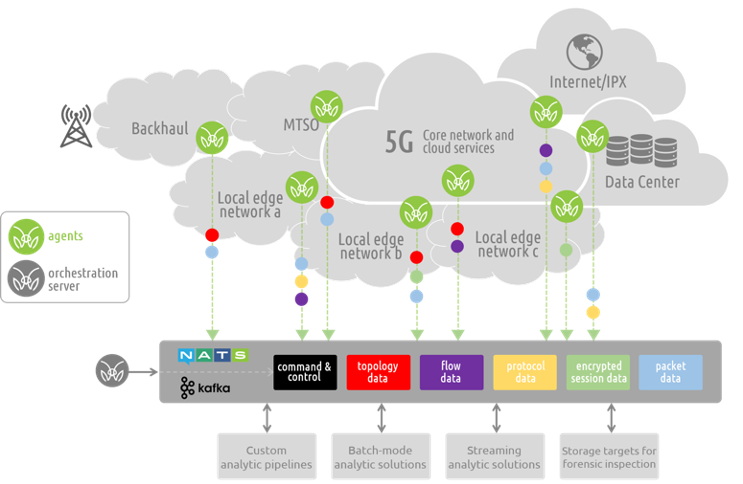
5G network architectures are redefining how resources are deployed, managed and utilized within a communications network. A fair blanket statement regarding these changes is that 5G is taking full advantage of cloud-native and virtualization technologies - even pushing them to the next level. These range from cutting edge, revolutionary 100% cloud native deployments from new entrants such as Rakuten, to the more measured non stand-alone (NSA) and hybrid architectures being deployed by the existing wireless service providers. One thing is clear- the days of capital-intensive dedicated physical infrastructure is meaning less and less as cloud-native technology is used to deploy dynamic, service-oriented, and highly scalable resources to deliver on the promises of 5G.
But, what does this mean for data visibility?
Read More
Tags:
network engineering,
network preformance,
Real-Time Monitoring,
mantis
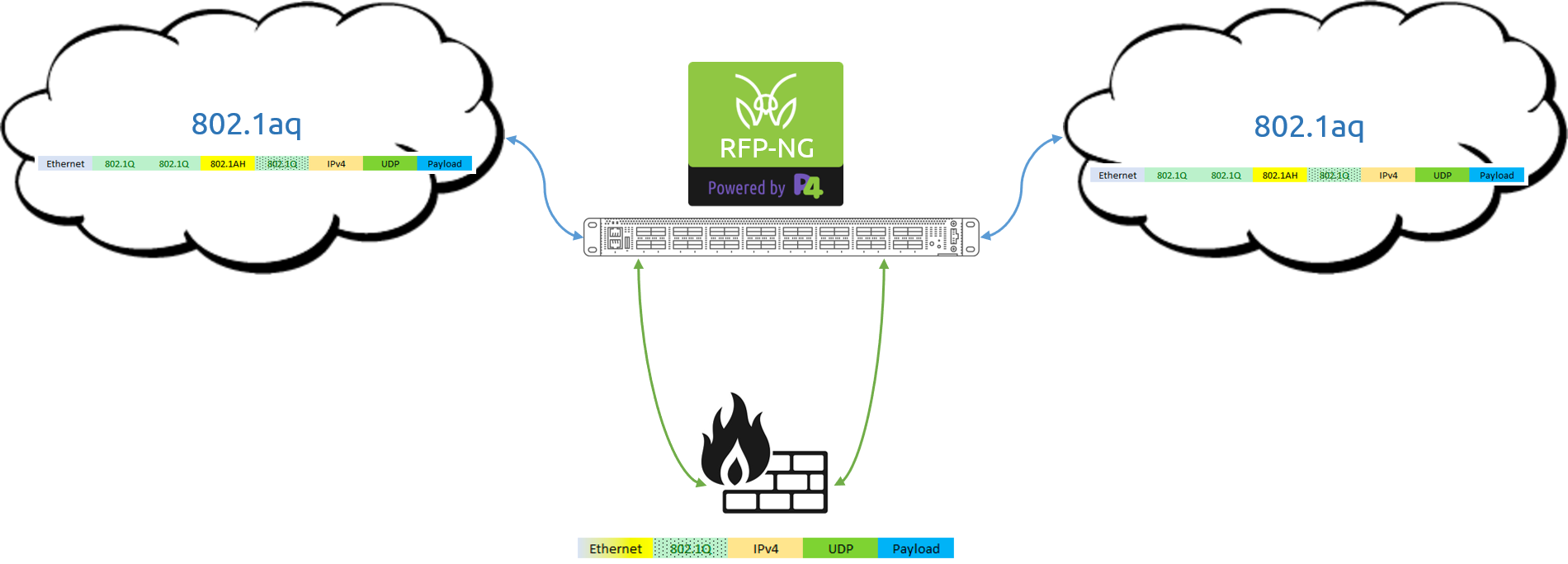
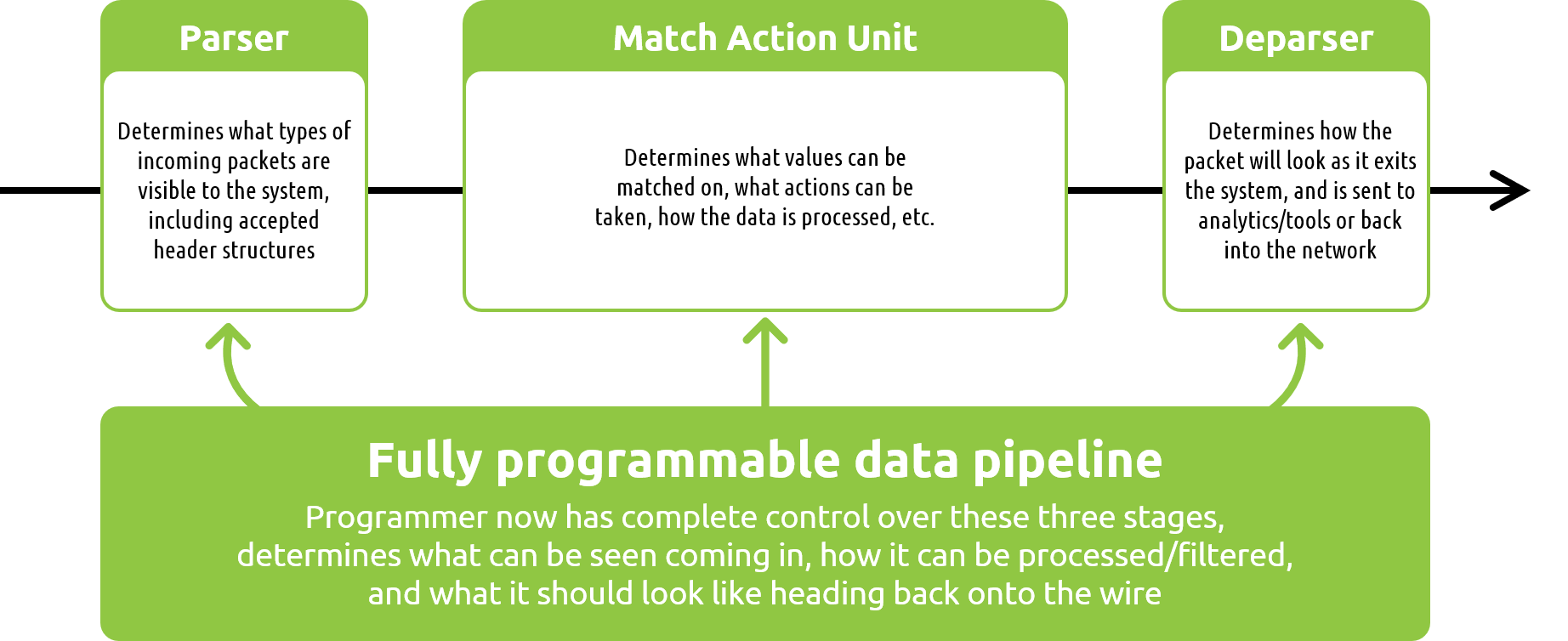
This is a continuation of our blog series on the advanced functions for network visibility solutions with fully programmable data pipelines. Read our introduction to the series here.
Another great example of the power behind fully programmable pipelines is the ability to gain insight into the actual visibility solution itself. Solutions such as the MantisNet RFP-NG are able to leverage the processing logic of these pipelines to better visualize what types of events are unfolding on the wire over time and provide metrics related to the rules that are running. Once again, let’s simplify things here for a moment to best understand this concept….
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis
This is a continuation of our blog series on the advanced functions for network visibility solutions with fully programmable data pipelines. Read our introduction to the series here.
The biggest elephant in the network visibility room has always been the fact that you don’t know what you are missing. If there are packets with structures that fall outside of your fixed-function ASIC-based chip/solutions capabilities (and trust me, there always are), you are not only going to drop those packets, but you also have zero indication that you just missed a packet. The packets simply fail to parse, and you will not know that you are missing that information. You can’t control, what you can’t see.
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis
This is the first in a series of blog posts that examine the topic of fully programmable data pipelines and their potential to transform the network visibility industry. Within this series we will be discussing what a programmable pipeline actually is, how solutions built with programmable pipelines differ from what has been available on the market, and the advantages organizations stand to gain by adopting such solutions.
Before we begin, it is important to note that programmable pipelines are here today due to a key innovation made in the networking switch world- the development of a programmable ASIC/chip. This new chip, along with the open source language used to program the chip, have allowed a new breed of network visibility solutions to emerge. These solutions are dramatically different than legacy network packet brokers- solutions which are built using static, fixed-function ASICs.
Throughout this blog series we will make sure to cover the differences between these two solutions, as well as highlight the advanced visibility functions that are now available to users for the first time thanks to fully programmable data pipelines.
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis
DNS. A necessary mechanism that makes global network communications work, connecting services to the internet or private network, thereby powering our digital lives can also present confounding and problematic engineering challenges with cybersecurity implications. Site not responding, nefarious applications, applications not resolving, broken network connectivity…many initial responses are Is it DNS? it’s DNS, “It’s always DNS”.
DNS, the domain name system, connects domain names to IP addresses that locate and route information and traffic from a source location to a client can be the bane of many network and cybersecurity engineers as they maintain networks or investigate potential threats on the network.
We’ll look at this critical network component, its threat value and how you can make DNS an actionable component
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis,
cybersecurity
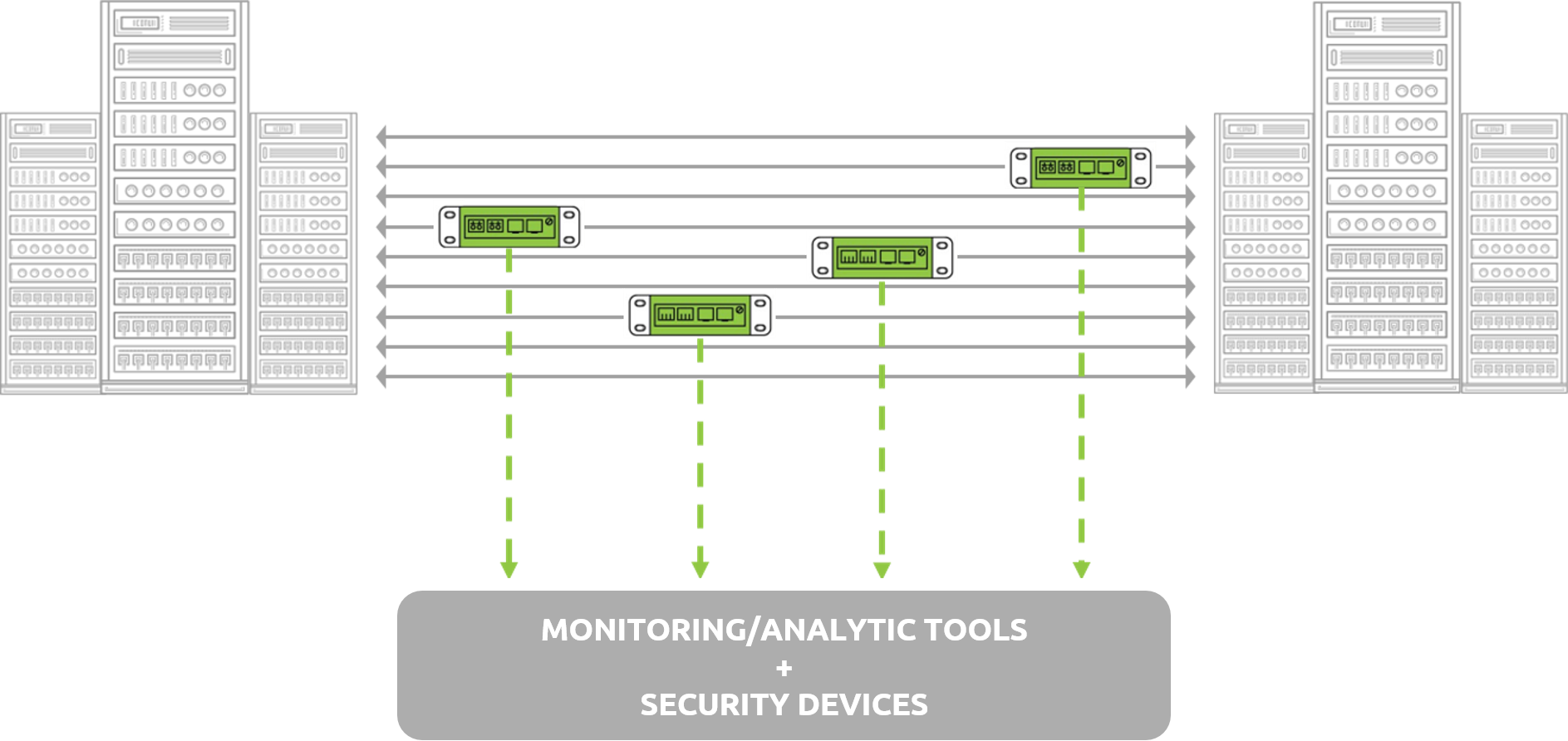
A new class of highly intelligent Virtual Switches and Next-Generation Packet Brokers (NPB) is on the rise.
Cloud computing and software-defined networking (SDN) have made development and operations teams far more aware of the importance of their networking infrastructure than ever before. In the age of DevOps, private, hybrid, and public cloud computing - the network is the fabric that holds the compute infrastructure together.
Read More
Tags:
network engineering,
network preformance,
cyber security
While deploying network monitoring tools, IT managers are often faced with questions, such as: "Can we do this and still ensure that we aren't impacting the production network?" or "Can I make sure that I can see 100% of network traffic?" or "What is the best way to get data into my monitoring and test tools?"
Read More
Tags:
network engineering,
test/lab automation,
network preformance,
cyber security,
IT operations