This is a continuation of our blog series on the advanced functions for network visibility solutions with fully programmable data pipelines. Read our introduction to the series here.
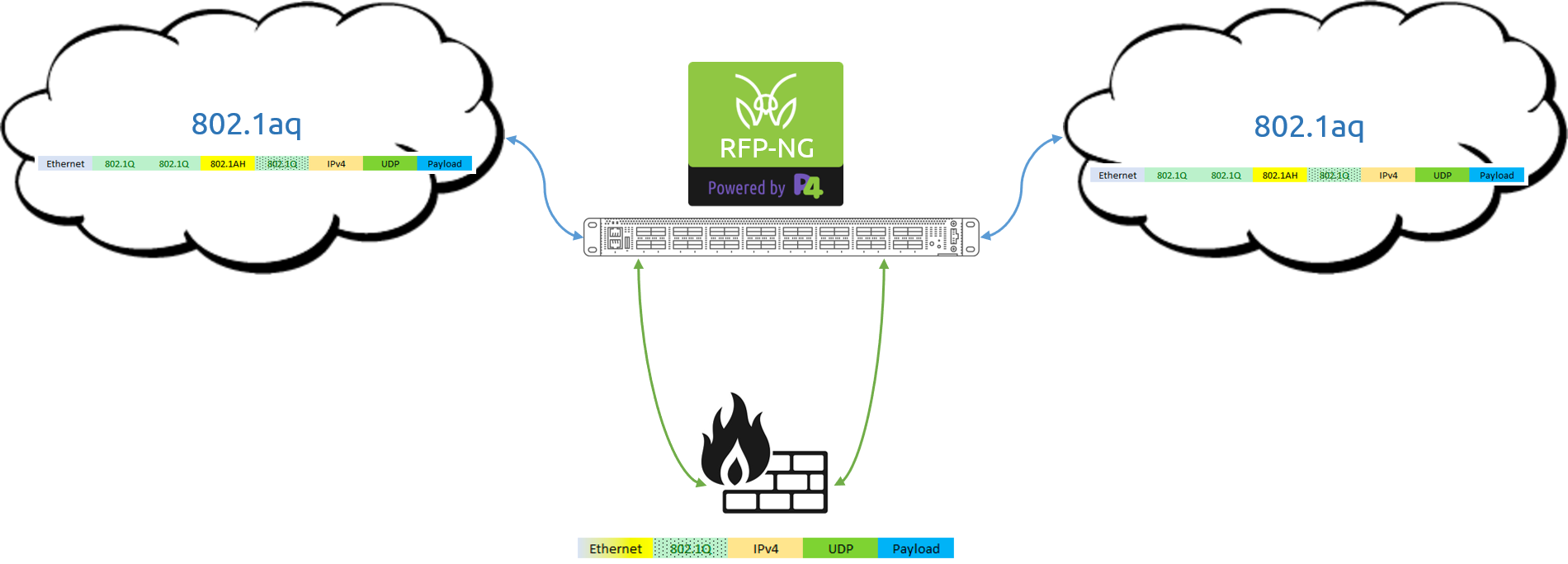
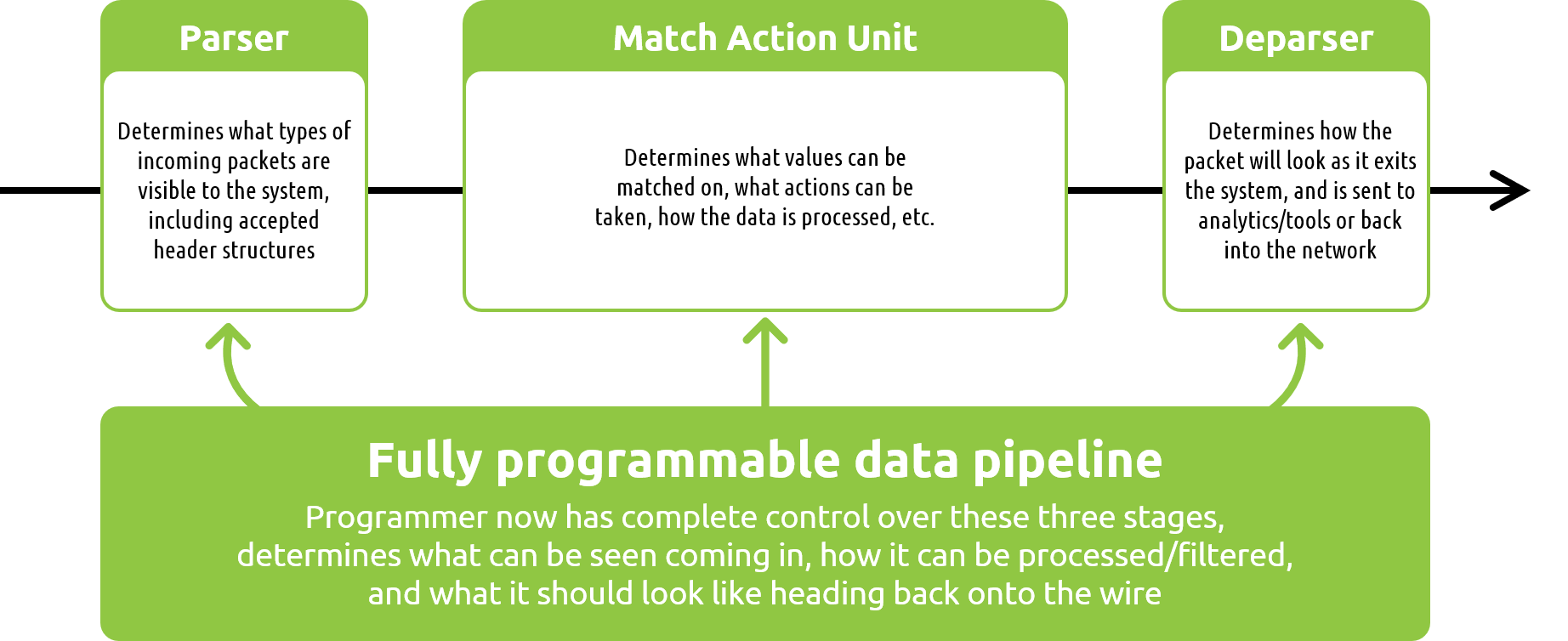
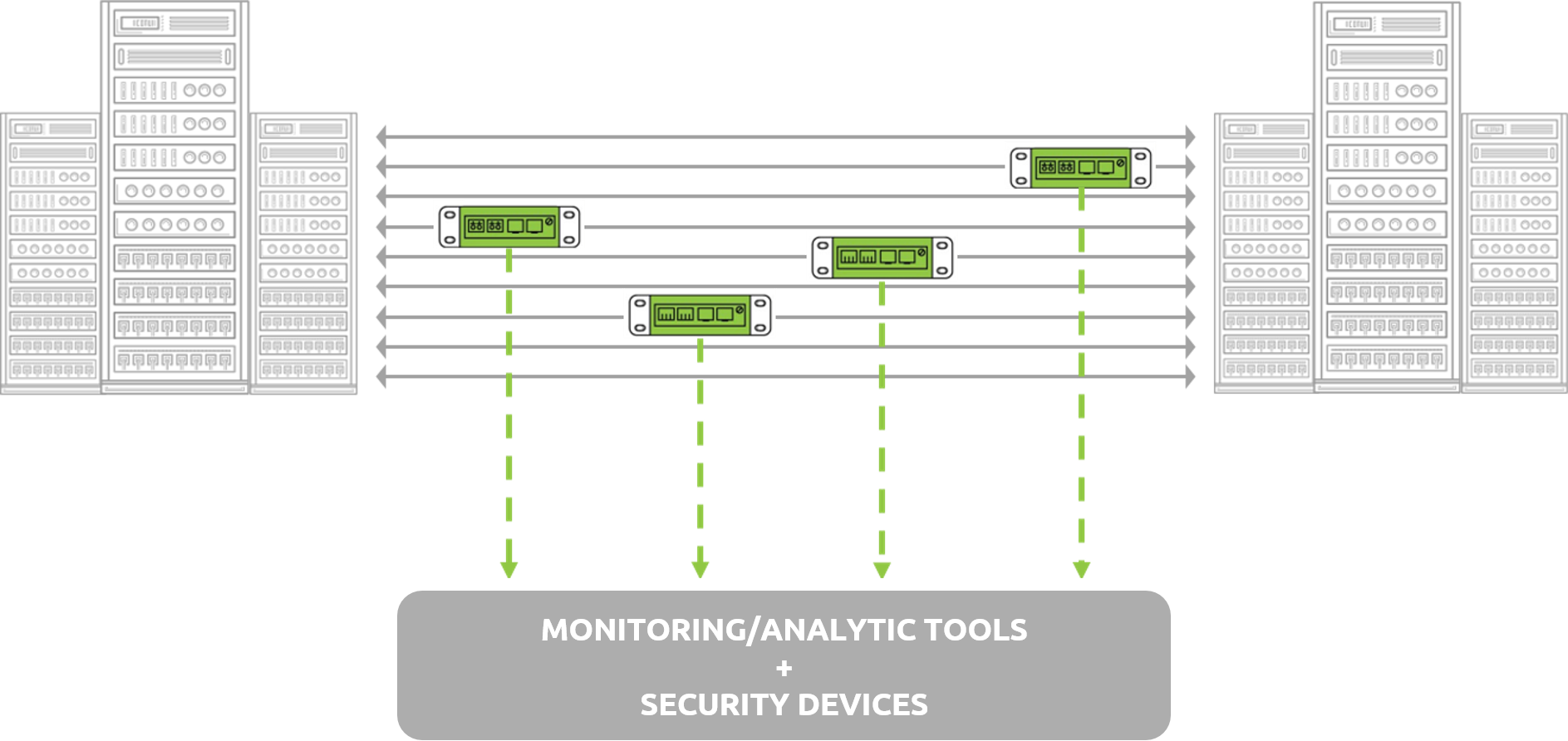
Another great example of the power behind fully programmable pipelines is the ability to gain insight into the actual visibility solution itself. Solutions such as the MantisNet RFP-NG are able to leverage the processing logic of these pipelines to better visualize what types of events are unfolding on the wire over time and provide metrics related to the rules that are running. Once again, let’s simplify things here for a moment to best understand this concept….