DNS. A necessary mechanism that makes global network communications work, connecting services to the internet or private network, thereby powering our digital lives can also present confounding and problematic engineering challenges with cybersecurity implications. Site not responding, nefarious applications, applications not resolving, broken network connectivity…many initial responses are Is it DNS? it’s DNS, “It’s always DNS”.
DNS, the domain name system, connects domain names to IP addresses that locate and route information and traffic from a source location to a client can be the bane of many network and cybersecurity engineers as they maintain networks or investigate potential threats on the network.
We’ll look at this critical network component, its threat value and how you can make DNS an actionable component
from intelligent network sensors to identify and apply DNS to network security monitoring and cyber defense through SIEM (e.g. Splunk), other cybersecurity analytic workflows and network management platforms. Jump below to a broader list of applicable DNS observability, detection and response uses.
DNS – a critical information transfer component
Network communications rely on DNS to connect to network resources. However, because DNS primarily uses the User Datagram Protocol (UDP) and DNS responses typically do not use any form of cryptographic protections, the implementation of DNS lends itself to many attack vectors such as network packet sniffing, hijacking, cache poisoning, DDoS and man-in-the-middle attacks. Consequently, and because DNS is critical to the operation of networks: legitimate users and applications rely on these services, accordingly malfunctioning systems and/or malevolent actors can seriously interfere with operations that are reliant on DNS.
Given the increasing level of sophistication and wherewithal on the part of the bad actors; it is more important than ever to have the best tools and capabilities to accurately and efficiently monitor, identify and remediate DNS anomalies and issues as quickly as possible. The previous generation of DNS tools mostly relied on, endpoint agents, data-at-rest (logs), lossy or unreliable data sources (NetFlow) that could not deliver real-time, continuous monitoring or relied on visibility technologies and could be incomplete and unreliable (SPAN and mirror ports). Additionally, many of these legacy solutions also required expensive hardware such as packet brokers, duplicative monitoring fabrics (networks) or purpose-built and inflexible hardware that did not operate continuously in real time and competed for bandwidth, storage, power and processing resources.
Intelligent Network Sensors: upgrading the legacy eyes and ears of the system
In general, the sensor component can be any type of probe, packet broker or traffic visibility system to capture or sample network traffic. However, legacy sensor technologies can no longer keep up with the demands (speed, scale, complexity) of today’s IT landscape – consequently new forms of network sensor technologies need to be deployed. Regardless of the sophistication of the monitoring and analytics system, legacy technologies can suffer from the syndrome of “garbage in – garbage out” where systems using unreliable or incomplete data can leave organizations seriously exposed. However, new software-based network sensor technologies are: reliable, lossless, always available and able to accommodate any network protocol and continuously operate in real-time where ever they are needed.
These new software-based sensor technologies can monitor, filter, collect and process DNS (among many protocols) intelligence continuously and in real time. They can also deliver flexible forms of telemetry; their output can support both legacy protocols (NetFlow or IPFIX) as well as new stream-based systems and continuously publish streaming forms of highly efficient, standardized, reliable and secure serialized metadata into next-generation event-based architectures, and streaming analytics-based workflows.
|
Legacy Network Visibility |
Software Based Network Sensor Solutions |
|
Packet broker (NPB) & packet capture (PCAP): - packet broker and dedicated monitoring fabric-based approaches. |
Software based and cloud native: - Ease of deployment and continuous inspection of network traffic; anywhere, at any speed - in network infrastructure, on-rem (appliances) or as a containerized cloud services (SaaS).
|
|
Log or off-line, file-based, write-through disk architectures: -Non-continuous, non-real-time file based or endpoint-based systems subject to “zero-day” gaps, and corruption.
|
Network based, data-in-motion monitoring: |
|
NetFlow or IPFIX telemetry: - Lossy, sampled, potentially unreliable, inaccurate “best efforts” capabilities of network switches and routers to generate legacy NetFlow or IPFIX telemetry. - Requires purpose-built, expensive, inflexible generator-collector systems capable of delivering predetermined telemetry formats |
Metadata w/ event-driven architectures: - Generate and publish telemetry metadata into both legacy data formats for backward compatibility as well as new more efficient forms of metadata (JSON, Avro, Protobuf) into streaming message buses (Kafka, MTTQ, etc.) and analytics pipelines, resulting in lossless sampling for complete situational awareness |
DNS for NPM, SIEM, visualization and analytics
The DNS analytics workflow needs to support a range of capabilities.  From baseline, simple,
From baseline, simple, 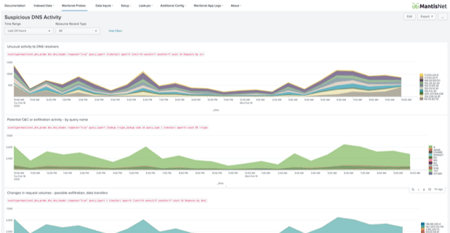 observations, and status reporting, to complex analytics requiring complex follow-on processing and enrichment with third-party and time-series data. Simple inspection and analysis of DNS traffic can reveal a lot about the stability and security of the network. More advanced, DNS derived analytics allows for new levels of indicators of compromise (IoC) and anomaly detection and can be further combined with a variety of external data sources; whitelist, blacklists, IP reputation, and inventory-related data, DNS server data and resource records for enrichment and correlation providing deeper contextual and situational awareness.
observations, and status reporting, to complex analytics requiring complex follow-on processing and enrichment with third-party and time-series data. Simple inspection and analysis of DNS traffic can reveal a lot about the stability and security of the network. More advanced, DNS derived analytics allows for new levels of indicators of compromise (IoC) and anomaly detection and can be further combined with a variety of external data sources; whitelist, blacklists, IP reputation, and inventory-related data, DNS server data and resource records for enrichment and correlation providing deeper contextual and situational awareness.
Continuously monitoring and visualizing the DNS traffic in real-time for observability is key to maintaining network stability, reliability, and security. The ability to continuously collect and process streams of DNS traffic within the analytics workflows and support a gamut of reporting tools and dashboards via highly efficient, reliable and secure telemetry is critical. This level of DNS sensing for decision and response making relies on detailed, reliable visibility made possible to better detect and intercept under-performing, malfunctioning and malicious or unwanted traffic and facilitate real-time decision loops.
To best monitor, analyze, and manage DNS communications requires a fast and accurate closed loop system: sometimes described as an OODA loop (observe-orient-decide-act) architecture. More specifically, such a system needs to combine real-time continuous and precise “sensor/sensing” functions that can be combined with and third-party data sources to support analytics workflows to address a complex range of decisions, and response capabilities that can evolve with the changing threat landscape.
Finally (and to state the obvious), to be useful, the accompanying analytics workflow and dashboards need to be easy to use, intuitive and utilize open and extensible supporting a range of analytic tools as well as be accommodating to more complex analytic workflows (incorporating such things as ML and AI functionality) allowing for new levels of visibility and interoperability across business teams as the operational and threat landscape evolves.
Next steps to implementing DNS monitoring, detection & response
By combining continuous sensing with highly efficient metadata and advanced analytics, MantisNet enables organizations to leverage valuable DNS traffic to best ensure their networks are more efficient, reliable and secure. With MantisNet solutions feeding SIEM, NPM and other analytic solutions, DNS traffic can be monitored and processed with a far higher degree of speed and precision than previously possible. In addition to providing real time, continuous visibility MantisNet provides extensibility and investment protection by supporting streaming event processing analytics, native interfacing with AI, deep learning and machine learning services to enable dynamic, automated control of the networks to detect and preempt potentially malicious traffic or misbehaving devices and connections continuously in real-time and/or isolated for purposes of testing, operations, maintenance, security, or remediation.
Here are just some examples of DNS observability and analytic uses that can be employed at your organization:
Foundational DNS functions for observability and analysis
- Technical investigations, forensic recording and analysis
- Network inventory and audit
- Qualitative, volumetric and frequency analysis of DNS events
- Authentication and validation of network access - whitelisted and blacklisted IP addresses
- Payload inspection - identification of malicious traffic, malware detection and analysis
- Domain Name to IP Resolution: Determine what IP address a Fully Qualified Domain Name (FQDN) or base domain name, resolves to
- IP to Domain Name(s) Resolution: Resolve an IP address to a domain name.
- IP Address to Domain names: inspect (sub)domain associations
- Investigate the hostname/FQDN associations
- Determine what domains are associated with specific name servers
- See what name servers are associated with specific domains
- Determine if specified hostname is in other top-level domains (TLD) and see if variations exist in other top-level domains
Advanced DNS observability and analytic functions:
- Identify misconfigured endpoints
- Inspect communication patterns across networks
- Scan detection and worm propagation
- Outlier Detection and Volumetric Anomaly Detection (DDOs and DrDoS)
- Identify clients and resolve potentially malicious domain names.
- Identify stale resource records.
- Identify frequently queried domain names and talkative DNS clients.
- View request load on DNS servers,
- Query DNS errors,
- Monitor DNS errors affecting server performance
- View DNS registration failures
- Detect domain spoofing
- APT Event Detection: reconnaissance, infiltration and exfiltration
- Botnet detection
- Tunneling and other non-DNS over port 53
- DGA Detection
- Squatting Detection
- Dark DNS -rogue DNS infrastructure
- DNS NXDOMAIN and Subdomain exhaust
- Detect potentially suspicious Newly Observed Domains (NOD)