Announcing the MantisNet Network Stream ProcessorSM App for Splunk
We’re excited and proud to announce that the MantisNet Network Stream ProcessorSM (NSP) App for Splunk is now available.
The App enables ingestion of streaming network metadata using key-value pairs: a powerful, new form of serialized metadata produced by MantisNet sensors. Customers can now access, integrate and manage these new forms of lossless, ultra-efficient, ultra-accurate and high-resolution metadata, to support continuous real-time network detection and response in Splunk.
Using key-value pairs derived from network traffic turns networks into powerful data science tools; delivering continuous, real-time visibility which is more detailed and reliable as compared to logs or other network monitoring technologies that only focus on commonly used protocols and well-known fields for analysis. 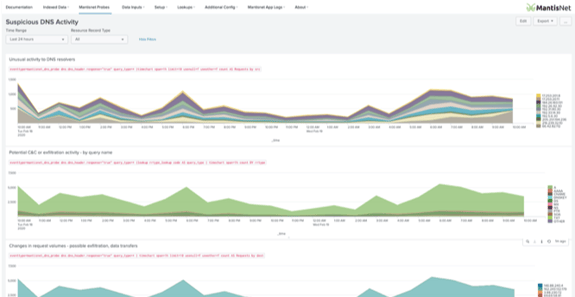
 MantisNet Containerized Visibility Fabric (CVF) sensors can identify, extract, and process complex protocols and allow for the detailed inspection through the MantisNet NSP App for Splunk, which provides network and cybersecurity operations teams with more context into network communications (“conversations”) at the kernel level.
MantisNet Containerized Visibility Fabric (CVF) sensors can identify, extract, and process complex protocols and allow for the detailed inspection through the MantisNet NSP App for Splunk, which provides network and cybersecurity operations teams with more context into network communications (“conversations”) at the kernel level.
The MantisNet CVF sensors and NSP App for Splunk enable comprehensive visibility into all network traffic including cloud native or microservices architecture traffic, nested data structures, and optional fields, continuously and in real-time. Furthermore, the serialized network metadata is structured in the form of key-value pairs- a more efficient data format for transmission, storage, analysis and processing to feed AI / ML models, anomaly detection as well as alerting, and automated or orchestrated response systems.
DNS and beyond
Discover the power of data-in-motion and metadata: begin your journey by getting deeper, richer insights into network traffic and behaviors. Start with the community version of the MantisNet NSP App for Splunk that includes a trial offer of our CVF network sensor. The app is free to download and comes pre-configured with visualizations and reports for DNS traffic metadata produced by MantisNet’s CVF network sensor.
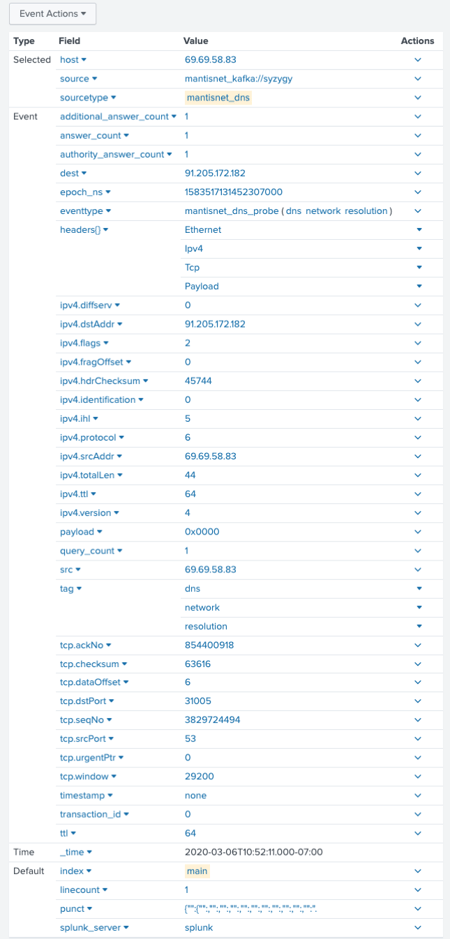
The MantisNet NSP App used in conjunction with the MantisNet CVF sensor enable you to easily generate and ingest structured DNS metadata into Splunk. DNS is a critical component that engineering, operations and cybersecurity teams rely on to monitor and analyze networks for performance and operational issues as well as to identify anomalies and hunt for indicators of malicious activity (TTPs). We’ve previously blogged on the importance of DNS observability and analytic workflows. While other sensors and analytics tools only pick off certain fields and functions and report those statically defined well known, well-worn DNS fields the MantisNet CVF sensors and NSP App enable comprehensive visibility into all DNS traffic including nested DNS data structures and optional fields, continuously and in real-time.
The NSP App supports ingestion of MantisNet streaming metadata via multiple formats and methods – Kafka, JSON, TCP or HTTP Event Collector.
Looking for more than just streaming DNS metadata? Numerous additional network protocols (HTTP/S, DHCP, GTP, etc.) and advanced CVF processing engine functions are supported using premium versions of the MantisNet CVF and NSP App. Premium version customers can access additional capabilities and ingest virtually any known network protocol, as well as the ability to detect and dynamically process any new or previously unknown type of network traffic.
Turning the corner on managing streaming network data
The future of comprehensive, real-time continuous detection and response is now becoming a reality. The MantisNet team is dedicated to supporting today’s best in class tools as well as delivering powerful data science capabilities to dev-ops, net-ops and sec-ops teams. As technologists with deep backgrounds in network engineering and signals intelligence it was fundamentally important to develop an App that can exploit new, more powerful, forms of MantisNet derived network metadata, enabling the Splunk community to seamlessly ingest, organize and manage it for more accurate, efficient and reliable follow-on analytics and orchestration. The MantisNet Network Stream ProcessorSM (NSP) App for Splunk natively ingests streaming metadata output from MantisNet’s nimble, scalable and performant Containerized Visibility Fabric network sensors, that can be placed anywhere on any virtual or physical network.
MantisNet CVF sensors dynamically identify, extract and stream detailed metadata for ALL or ANY SPECIFIC traffic of interest into Splunk, enabling organizations to access and manage the ingestion of that data into Splunk. The MantisNet CVF sensor and NSP App for Splunk delivers all the network intelligence organizations want, when they want it. It enables users to target network traffic of interest, at wire-speed, and organize the resulting network protocol metadata in the form of structured key-value pairs for efficient ingestion into Splunk.
MantisNet’s App and sensor capabilities provide tremendous value for a broad spectrum of applications and use cases (DevOps, NetOps, SecOps, Fraud Detection and GRC). Organizations on the forefront of adopting streaming analytics, event-based architectures, orchestration and (AI / ML enabled) automation will derive the greatest benefits due to MantisNet’s advanced forms of ultra-reliable, ultra-efficient, ultra-accurate, high resolution, real-time streaming metadata making network traffic more observable and actionable. We think this is an important step towards better identifying anomalies, combatting threats and managing the exponentially increasing volumes of data that flow through network and security tools that formally required require manual or offline storage and forensic, asynchronous analysis. Providing access to continuously streaming network metadata, in real-time, provides critical intelligence feeds into the analytic workflows, and orchestration systems that are crucial to helping to manage the problems of growth and data-decisioning. What got us to where we are today in network management and security will not get us to where we need to go for tomorrow’s network and cybersecurity challenges.
The MantisNet Network Stream ProcessorSM App for Splunk was developed by BaboonBones, winner of Splunk’s 2018 Revolution Developer Award, and the developers behind the most downloaded and production installed Apps on Splunkbase.
“MantisNet’s approach to generating new forms of network traffic visibility and their recognition of the power of the Splunk ecosystem is truly visionary. With the goal of enabling Splunk users to realize the goal of real-time detection and response, MantisNet worked with us to develop an App that enables the Splunk data platform to ingest and exploit the exciting new forms of streaming network metadata that MantisNet provides” said Damien Dallimore, Managing Director at BaboonBones.
Explore more with these related links:
- Download the Network Stream Processor App for Splunk from Splunkbase
- Splunk partner+ profile
- MantisNet Splunk solutions


