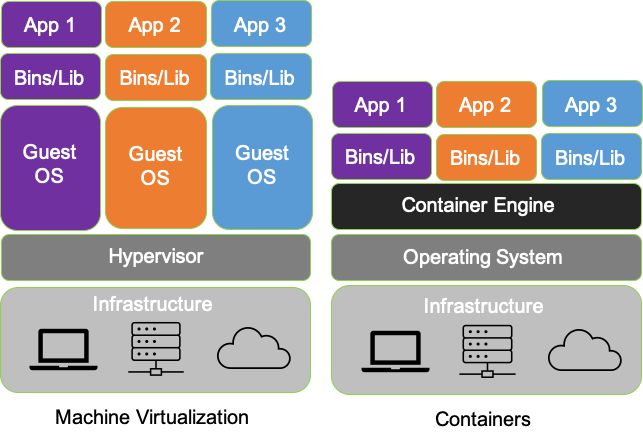
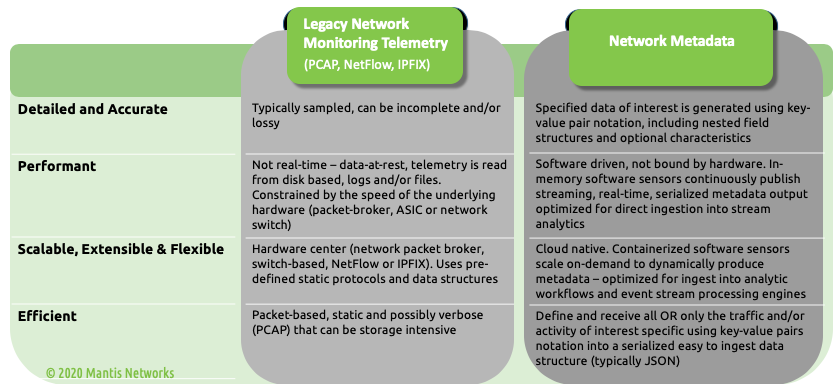
In our last post “Introducing the MantisNet CVF: Solving Cloud Native, Serverless, Observability Challenges“ we provided an overview of the Containerized Visibility Fabric (CVF) capabilities and made some assertions about how revolutionary and disruptive cloud-native technologies are, the resulting opacity problems, as well the art of the possible insofar as enabling next-generation observability.
In this installment we’ll go into more detail as to what exactly we mean by cloud-native observability as well as the significance, deeper implications of it, interoperability and investment protection. So, let’s revisit containerization, and by extension, why cloud-native observability is so revolutionary.
Read More
Tags:
Real-Time Monitoring,
Data-In-Motion,
mantis,
cybersecurity,
containers,
cloud native network function
Solving the opacity problem - Bringing clarity to traffic obscured by encryption.
There are many reasons that the use of encryption will continue to increase as it provides a method of privacy and security of communications and lowers the risk of information loss. However, encrypted session traffic does pose a challenge in achieving visibility and observability of network events for day-to-day operational management, risk detection and response, and lawful intercept scenarios.
How can teams better leverage the information contained in encrypted network traffic sessions for real-time network visibility?
Read More
Tags:
Real-Time Monitoring,
Data-In-Motion,
mantis,
cybersecurity,
containers
As we’ve shared previously - networks are the circulatory and nervous systems of your enterprise. Indeed; “the network is the computer”, and networks are an invaluable source of ground-truth. From a communications perspective, you can learn a lot by directly observing who is speaking, to whom they are speaking, the language they are using, the tone of voice, and the content of the communications. When it comes to network communications and metadata the analogies are obvious: in the case of DNS traffic- mapping URLs into IP addresses, and identifying underlying services and connected devices - in the case of TLS protocol, getting detailed insights into the encryption capabilities and device characteristics - likewise the GTP protocol provides geo-location specific information, and in the case of the MODBUS protocol, understanding the communications within industrial control systems.
Read More
Tags:
Real-Time Monitoring,
Data-In-Motion,
mantis,
cybersecurity
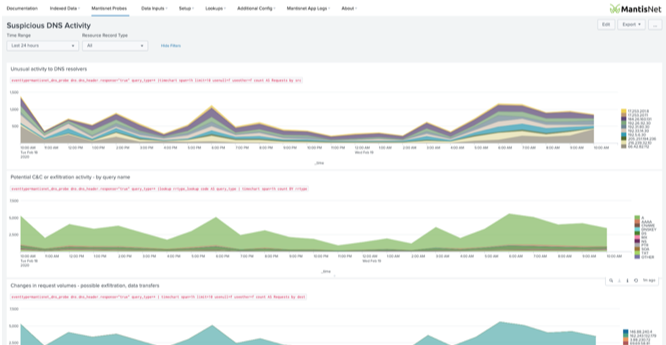
Announcing the MantisNet Network Stream ProcessorSM App for Splunk
We’re excited and proud to announce that the MantisNet Network Stream ProcessorSM (NSP) App for Splunk is now available.
The App enables ingestion of streaming network metadata using key-value pairs: a powerful, new form of serialized metadata produced by MantisNet sensors. Customers can now access, integrate and manage these new forms of lossless, ultra-efficient, ultra-accurate and high-resolution metadata, to support continuous real-time network detection and response in Splunk.
Read More
Tags:
Real-Time Monitoring,
DNS Monitoring,
Data-In-Motion,
mantis,
cybersecurity
Today we announce the publication of our Special Report: Reduce Risk with Real-time Interactive Remediation of Network Traffic. It contains a discussion and explanation of the emerging capabilities of technologies to enable real-time decisions based on live / streaming network traffic data to reduce cybersecurity and operational risk.
Read More
Tags:
cyber security,
Data-In-Motion,
mantis
As technologies advance and enterprise networks expand, administrators accountable for the overall health and performance of infrastructure accumulate more and more responsibility. CIOs are continually analyzing the problem of how to better monitor and secure the activity within their organization’s network.
Read More
Tags:
Real-Time Monitoring,
Data-at-Rest,
Data-In-Motion,
cybersecurity
We had the pleasure of supporting the Software Engineering Institute at Carnegie Mellon University’s conference, FloCon: Using Data to Defend. The presentations and discussions at the event provided validation that changes are coming to network and cyber security. More mathematical solutions are being developed to fuel machine learning and algorithms to combat malicious and other network traffic of interest. If you missed the event, an overview and video of our presentation is below.
Read More
Tags:
network engineering,
Real-Time Monitoring,
DNS Monitoring,
Data-In-Motion,
mantis
Before we can address the optimum method for responding to the continuously evolving cyber threat landscape, we need to understand the sources and types of data available from which we can understand and make decisions about the health and security of our systems.
Read More
Tags:
cyber security,
Real-Time Monitoring,
Data-at-Rest,
Data-In-Motion,
mantis