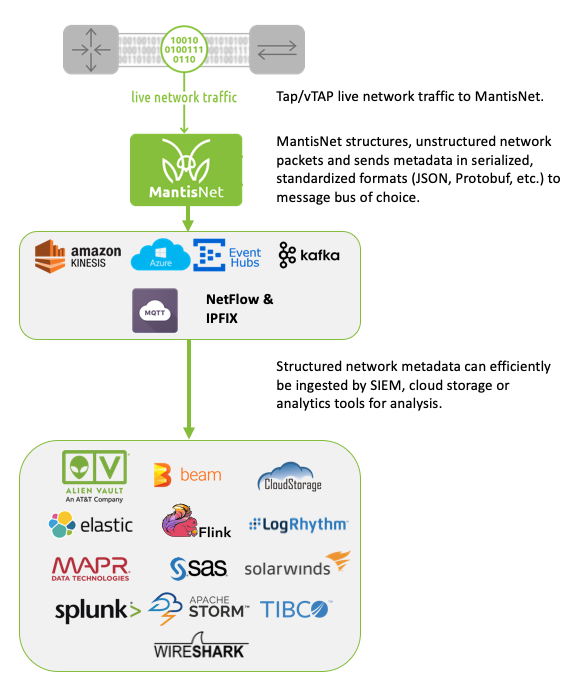
Digital transformation and the growing complexity of IT environments present new vulnerabilities that can be exploited by attackers for reconnaissance, delivering malicious payloads or to exfiltrate data. Using live network traffic for analysis to expose hidden malicious or anomalous activities and security threats among the complexity is fundamental for improved detection and response. So much so, that Gartner recently published an inaugural market guide for network traffic analysis (NTA), to help organizations understand what to look for (more on that later).
What is network traffic analysis (NTA)?
Network traffic analysis uses network communications and their protocols for detection, identification and analysis of cybersecurity threats and potential operational issues. As you’ll read, we propose doing this in real-time, with wire-speed network data and analytics to meet the demands of digital business and to gain an edge on reducing mean time to detect (MTTD) / mean time to respond (MTTR).