Solving the opacity problem - Bringing clarity to traffic obscured by encryption.
 There are many reasons that the use of encryption will continue to increase as it provides a method of privacy and security of communications and lowers the risk of information loss. However, encrypted session traffic does pose a challenge in achieving visibility and observability of network events for day-to-day operational management, risk detection and response, and lawful intercept scenarios.
There are many reasons that the use of encryption will continue to increase as it provides a method of privacy and security of communications and lowers the risk of information loss. However, encrypted session traffic does pose a challenge in achieving visibility and observability of network events for day-to-day operational management, risk detection and response, and lawful intercept scenarios.
How can teams better leverage the information contained in encrypted network traffic sessions for real-time network visibility?
For starters observing and generating metadata describing the encrypted traffic is an often overlooked, but powerful foundation for understanding the status, behavior, and health of the environment. Simply knowing the details behind what entities are exchanging encrypted traffic, the methods of encryption, and how those entities interact are incredibly useful - notwithstanding getting access to the encrypted traffic as well as the underlying (unencrypted) plaintext can all contribute to a more powerful strategy to increase observability of encrypted network sessions applicable to cloud-native monitoring. Furthermore, this level of visibility and observability delivered continuously and in real-time constitute a whole new range of possibilities for data-in-motion analysis (Security, APM, NPM) and special use-cases such as 5G network visibility of the infrastructure and monitoring across SBI and non-SBI interfaces.
The MantisNet Containerized Visibility Fabric (CVF) performs a variety of complex functions for monitoring encrypted traffic and cryptographic controls (for OpenSSL and GNU encryption libraries, up to and including TLS 1.3), anywhere in the infrastructure. This cloud-native, composable solution goes beyond capturing packets to extracting, processing and publishing new forms of encrypted session metadata to enable comprehensive cryptographic monitoring and supporting streaming analytic (AI & ML) workflows follow-on processing to bring clarity to obscured network functions.
CVF agents provide the ability to identify, extract and publish a wealth of encrypted session parameters, specifically the details of the TLS client - server exchanges, that providers need to meet most of their cryptographic visibility, management and security demands. Regardless if it is to identify, monitor or quantify encrypted exchanges or to ensure the reliability and stability of systems, or to differentiate legitimate cryptographic exchanges from potentially malicious unknown, unreliable or questionable traffic. The CVF architecture publishes all the metadata and traffic of interest needed to support analytics, decryption, storage and forensic analysis services.
CVF has solved the encryption problem for the majority of environments, enabling visibility into plaintext (unencrypted) traffic in those cloud native environments. Prior to MantisNet; applications needing to inspect encrypted traffic (security / malware analysis, APM/NPM, SRE or lawful intercept), required a time-consuming and potentially costly multi-step process: 1. Capturing or replicating the traffic 2. Storing the encrypted traffic, and 3. Running an (offline) decryption or analytic process. The MantisNet CVF supports a simpler, faster, more efficient way to access and inspect encrypted traffic and plaintext directly with a container-native agent co-residing in the cloud infrastructure where the encrypted traffic is generated and consumed.
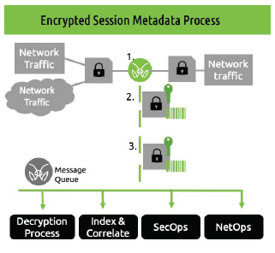 The process inspects and extracts information such as:
The process inspects and extracts information such as:
- Encrypted session metadata - client/server hello exchanges
- Encrypted session plaintext - providing plaintext prior to or post- encryption processes
- Encrypted traffic - for follow on decryption or forensic inspection
Learn more about the encrypted session visibility process.
Encrypted Traffic Session Visibility Use Cases
As you could expect; real-time, continuous observability, visibility and monitoring has significant benefits across a variety of applications. Here are just a few:
- 5G Network Visibility, Infrastructure and IoT – As commercial deployment of 5G SA and hybrid systems ramps up; there will be extensive use of encryption across the infrastructure, from the RAN to the Core. Not the least of which is across Service Based Interfaces (SBI) between the core network functions. Having the ability to not only introspect the traffic across these interfaces, but also extract session metadata and plaintext continuously and in real-time is essential to operating and supporting these systems and can help carriers and operators with their network detection and response, performance monitoring and lawful intercept needs.
- Fraud and Anomaly Detection - Detecting synthetic identities has become exponentially harder. The bad actors have very sophisticated tools that operate at speed and scale in order to generate synthetic endpoints so as to defraud and/or overwhelm security protections. Here too, inspecting and fingerprinting, the initiation of encrypted sessions and encrypted exchanges (even without getting access to plaintext) continuously and in real-time is an immensely powerful tool in detecting and combating fraud, validating IAM and UEBA activities as well.
- Network detection and response (NDR) / network traffic analysis (NTA)- Having the ability to quickly identify and drill-down on encrypted traffic to feed SOC analysis for the timely identification, detection and response to malicious traffic, nefarious entity behaviors and threat actors is critical. Seeing what is contained within the encrypted traffic from a network communications metadata, ciphersuite and payload perspective can mean the difference in prevention and response.