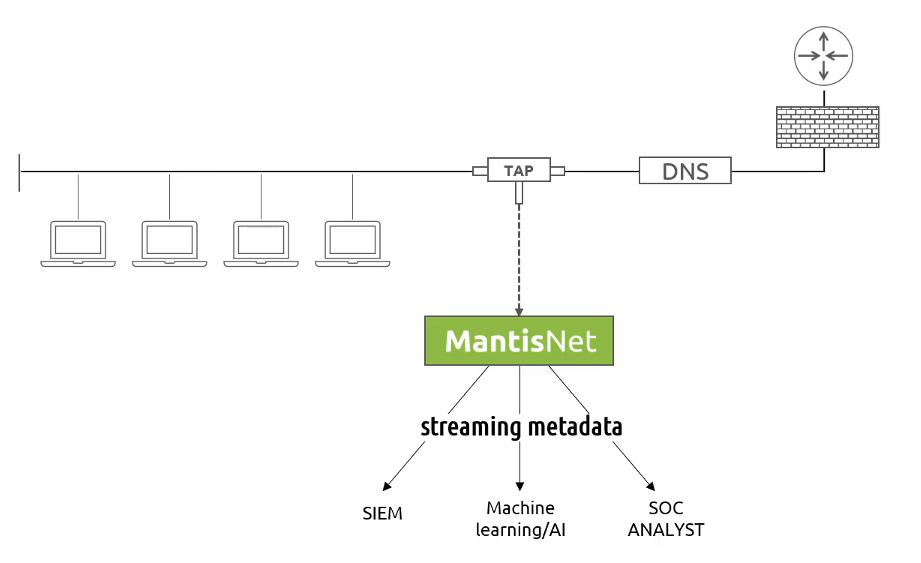
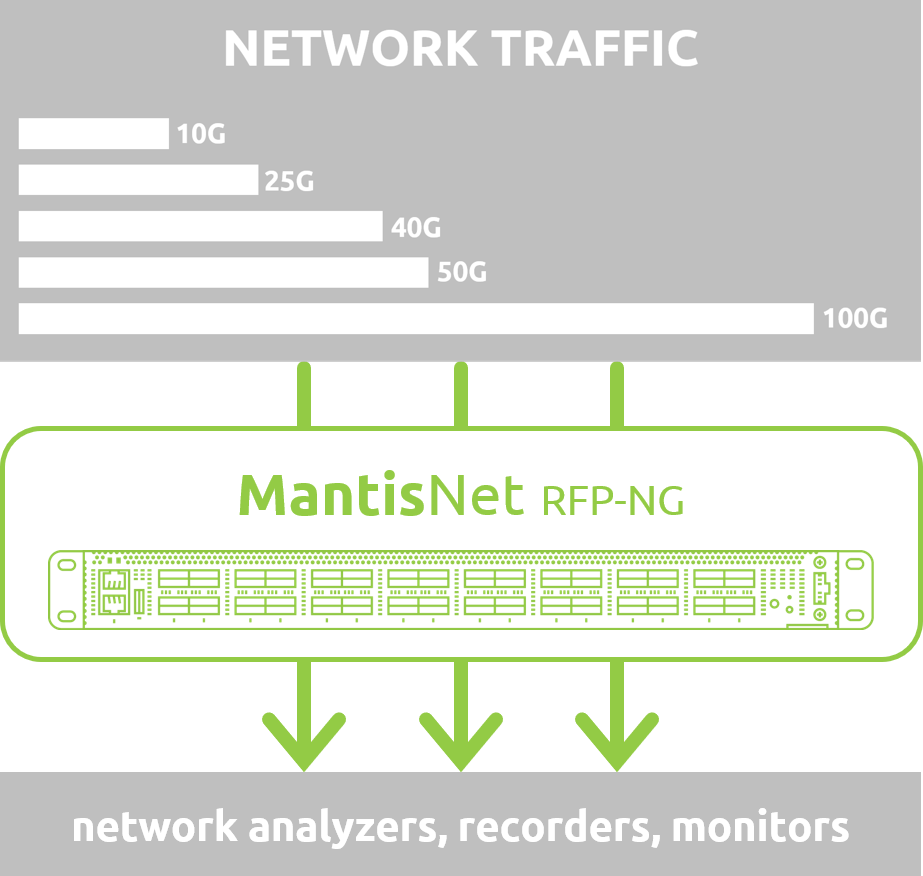
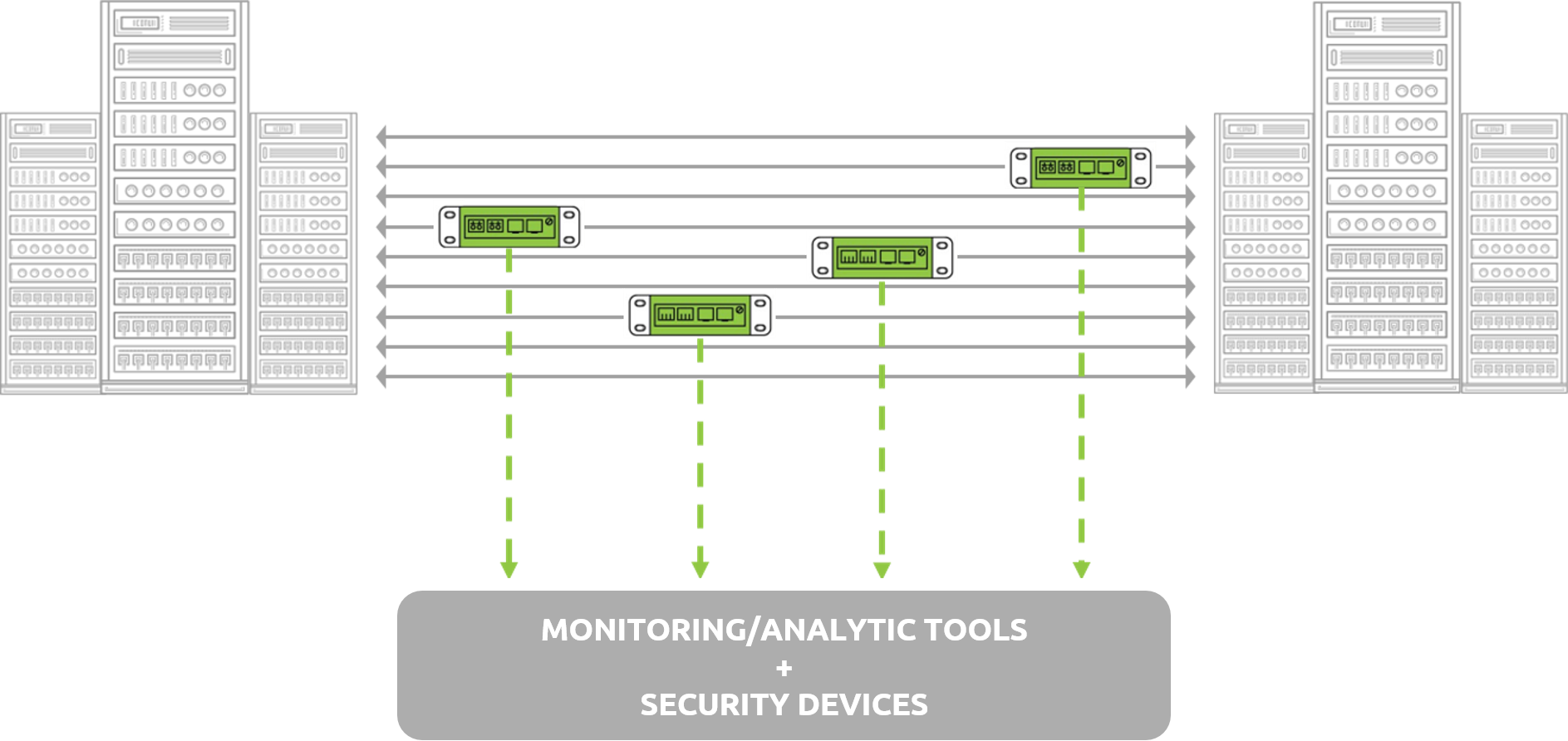
Before we can address the optimum method for responding to the continuously evolving cyber threat landscape, we need to understand the sources and types of data available from which we can understand and make decisions about the health and security of our systems.
MantisNet

Recent Posts
The Ultimate Cyber Security Strategy: Is Data-in-Motion The Answer?
Tags: cyber security, Real-Time Monitoring, Data-at-Rest, Data-In-Motion, mantis
Cyber Security Strategies that Make Data-at-Rest Obsolete
The world of cyber security is complex and misunderstood by a majority of the public. Even in IT, few people understand the complexities of a sophisticated cyber attack. It's this lack of understanding and the low number of experts in the field that give cyber attackers an advantage.
Tags: cyber security, Data-at-Rest
The Latest Verizon Data Breach Report: Your Data is Gone Within Minutes
Verizon released its latest Data Breach Investigation Report (DBIR) highlighting the latest trends in malware and cyber crime, covering 53,000 incidents and 2,216 confirmed breaches. The report reveals that botnets are the most widespread, dangerous attacks to date. The number of botnet attacks reported was so numerous that all 43,000 breaches (mainly on financial data) were excluded from overall statistics and given a separate section of its own. With botnet breaches on the rise, Verizon's report confirms that monitoring network traffic is more important than ever.
Continuous DNS Monitoring: A Real-Time Building Block for SOC Analysts
Identify and Defend Against Credential Stuffing and ATO Attacks
Tags: network engineering
Network Monitoring Step 2: The Next-Generation of Packet Brokers
Cloud computing and software-defined networking (SDN) have made development and operations teams far more aware of the importance of their networking infrastructure than ever before. In the age of DevOps, private, hybrid, and public cloud computing - the network is the fabric that holds the compute infrastructure together.
Tags: network engineering, network preformance, cyber security
Tags: network engineering, test/lab automation, network preformance, cyber security, IT operations