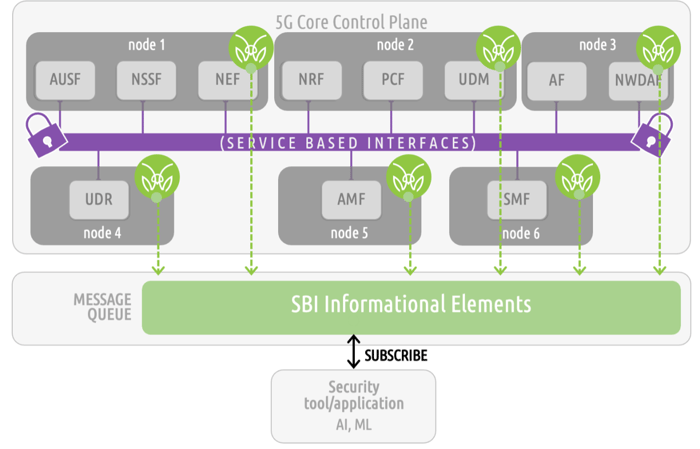
How to Get Visibility into 5G SA Ephemeral and Cloud-native Network Resources
Cloud native and containerized architectures are becoming the de facto design standard for 5G networks and applications. In the telecommunications industry, the players are focused on building out 5G Stand Alone (SA) deployments to deliver the promise of faster connection speeds to enable IoT, medical, autonomous use cases - not to mention improved communications, support the streaming of real-time content and the promise of a myriad of new applications and services. As we work with Tier 1 operators, MVNOs and analytics providers we are encountering a staggering issue: they can no longer adequately monitor, correlate, and measure critical network and application communications events at the container level and across the infrastructure.
As we have illustrated through our demonstrations and proof of concept deployments of our Containerized Visibility Fabric (CVF) with telco and related technology suppliers, the most common phrases we’re hearing during the engagements are:
"Wow! This is showing us what we've been trying to manage around and lets us capture and correlate events we can't currently see [between and within containers]."
- VP Engineering, Responsible for service assurance solutions at a leading 5G MNO
Or another common one is:
"Until now, we haven't found a solution that can provide visibility into encrypted data exchanges occurring across SBA NFs [network functions]."
- VP Product, Visibility and Analytics company
When the task of observability or even basic visibility into containers or cloud-native communications within these environments is approached, we come across organizations that are trying to retro-fit legacy (TAP and PCAP based) visibility solutions to accomplish only what a truly cloud-native observability solution is able to do, OR they’re relying on service mesh metrics or the deployment of management tools to provide some form of instrumentation into these environments. Clearly these workarounds aren’t sufficient, scalable or sustainable for the service levels that 5G environments must meet and begs the following questions:
How can you best manage network and application bottlenecks when you can't:a) see critical elements / functions,
b) see the events they generate and
c) correlate the corresponding events with the resulting network and application communications?
How can you dynamically identify, measure, and manage these quickly provisioned and decommissioned (ephemeral) resources?
Here is how MantisNet provides visibility and observability into these containerized environments with our CVF. Using eBPF technology and advanced in-node processing our CVF provides detailed, continuous, real-time introspection and processing of events when and where they occur. The CVF is event driven, modular and composable; meaning CVF functions can be activated when and where they are needed. The resulting telemetry is produced in a serialized metadata format and continuously published / streamed in real-time via a message bus, using an open publish-subscribe architecture. This approach supports continuous visibility into ephemeral resources, dynamic topology inventory, flow statistics, protocol decoding, as well as the capture and filtering of network communications that is foundational for any security, infrastructure monitoring or management applications. Additionally, due to the cloud-native nature of CVF, it is resource efficient, extremely lightweight, 100% software driven and it provides significant cost and scalability benefits as compared to legacy visibility solutions.
Dynamic Topology and Inventory
Since the cloud enables seamless scalability and elasticity, these cloud-native and containerized resources are also subject to explosive provisioning and decommissioning of services to support the dynamic nature of the workloads generally this continuous, real-time provisioning and decommissioning has been difficult, or impossible, to inventory and view until now.
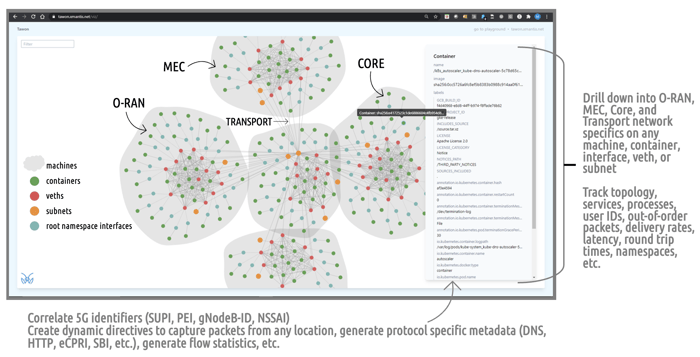
When deployed in the 5G environment the MantisNet CVF agents provide a dynamic topology visibility (see image above) of the containers, network resources and communications that make-up the services. Not only providing visibility, but keeping track of the dynamic and ephemeral inventory and the topology of those services as they are used (resources created/tasked) to support the myriad of network functions and services.
The importance of these capabilities is just beginning to gain serious attention.
In the above picture: the gray entities represent different portions of the 5G network from the RAN, MEC through to the Core/SBA- with the lines representing the network interfaces interconnecting them. The various dots represent the containerized and/or virtualized containers, virtual ethernets, subnets and root namespace interfaces.
Attribution for Security, Application and Network Performance
Since the CVF agents dynamically discover and monitor all the resources, events, and machines that they are associated and the resulting (metadata) telemetry contains unique flow identifiers, this provides visibility into network events that are occurring AND provides attribution of these events to a known originating source. The data streamed from the CVF agents is streamed to the management analytics workflow to provide the real-time data that can be used correlate those events to identify bottlenecks, as well as pinpoint security concerns across the cloud infrastructure.
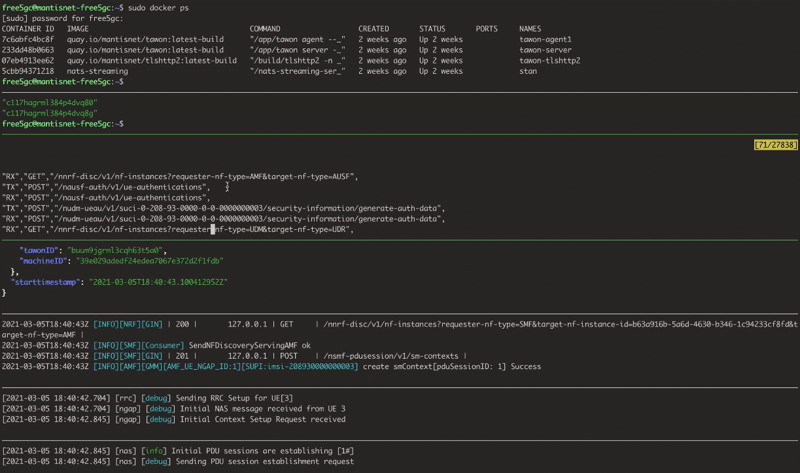
Another example, as shown in the screenshot below, is taken from a Free5GC demo environment. In the graphic we see the UE generated activity traversing the network from RAN to MEC/Core, demonstrating the capability of the CVF to monitor and generate timestamps for all events down to the network function. Since low latency is a heralded characteristic of 5G, having visibility into time-series metadata, latency and throughput information on the control plane is critical to maintaining the performance of the entire environment. In this example illustrating the AMF talking to the SMF you see messages in both directions ('RX' & 'TX' components) for visibility into the performance as the activity is occurring.
An additional benefit of the CVF is the in-node processing of network traffic or events where and when they occur. The CVF agent(s) can be deployed anywhere and directed to perform a variety of complex traffic/event filtering, protocol processing, packet capture, CNflowSM function, and TLS 1.3 encrypted session metadata extraction. This in-node processing capability means you can perform those activities – continuously and in real-time - without having to offload network/application data to a different cloud to perform analysis, potentially losing valuable time as well as incurring egress, storage and additional compute costs.
When it comes to the Core Service Based Interfaces (SBI) of 5G systems, our ability to overlay and capture encrypted traffic and provide the plaintext (payload) is proving to be a valuable solution to addressing the problem of SBI management.
Since the CVF resides on the network and can observe kernel-level events, and produce them in a form that can be correlated and easily ingested into follow-on analytics systems, these capabilities, puts the engineers and architects in the driver’s seat to better observe, detect and remediate a wide range anomalies, infiltration, data movement, performance deviations and other indicators of compromise that would otherwise have to “bubble up” to a higher layer of analytics. Having these continuous, real-time, capabilities at the kernel-level enables faster detection and identification of issues that can save significant amounts of time and critical resources.
We are finding that our clients really appreciate the MantisNet CVF for its simple, non-intrusive network deployment that provides highly valuable network and application telemetry when and where it's needed to manage and maintain 5G network services. We invite you to schedule a demo or an introductory discussion.
Additional Resources:
- White Paper: 5G and Cloud-Native Security
- Overview: Containerized Visibility Fabric
- Webinar: How 5G is Changing Network Visibility
- Blog: Gaining Visibility into the 5G SBA