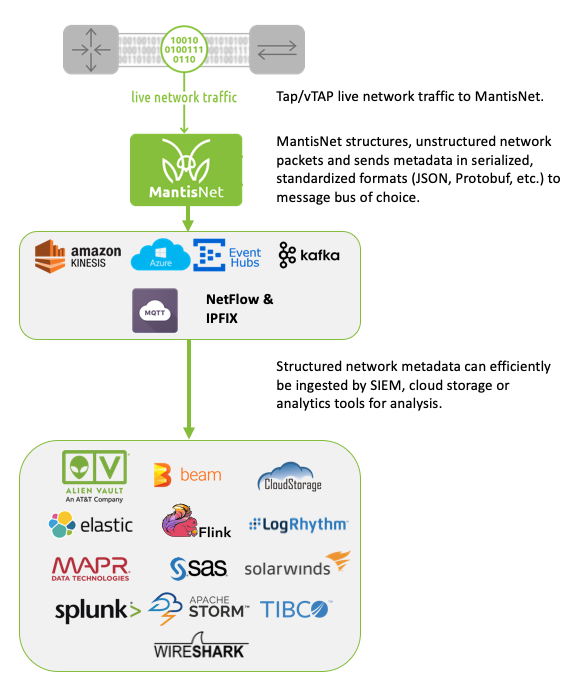
This is a continuation of our blog series on the advanced functions for network visibility solutions with fully programmable data pipelines. Read our introduction to the series here.
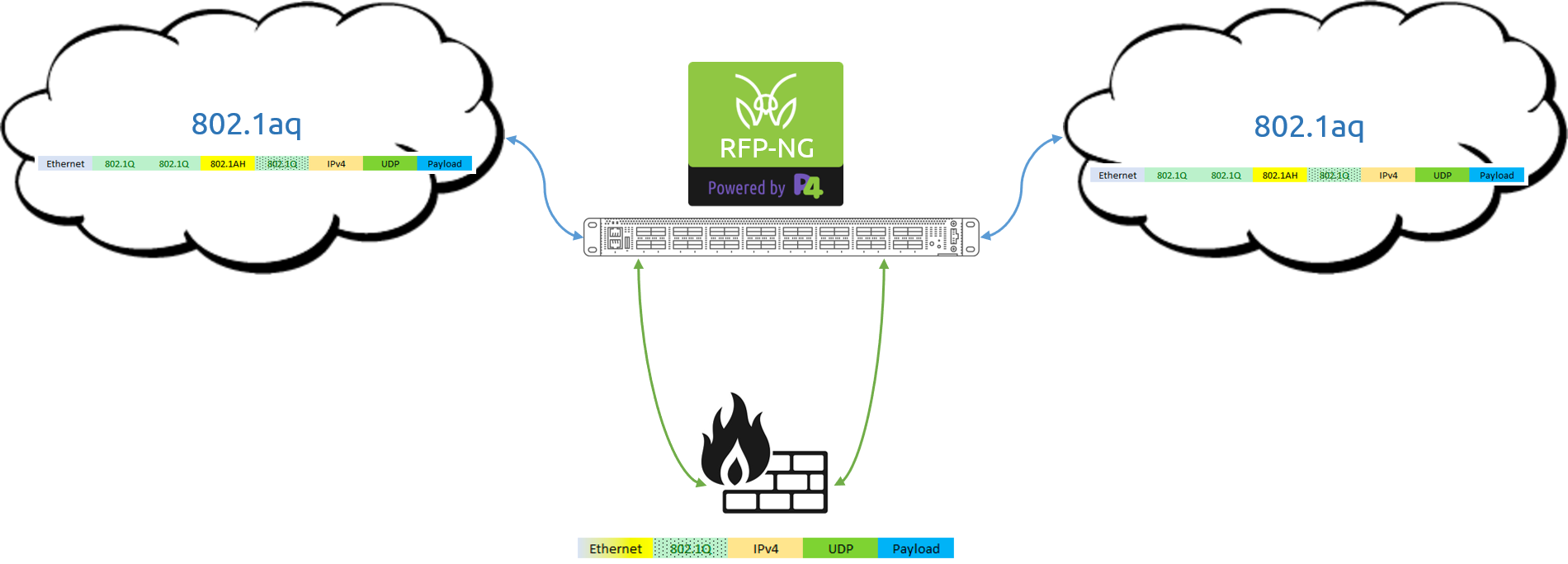
The biggest elephant in the network visibility room has always been the fact that you don’t know what you are missing. If there are packets with structures that fall outside of your fixed-function ASIC-based chip/solutions capabilities (and trust me, there always are), you are not only going to drop those packets, but you also have zero indication that you just missed a packet. The packets simply fail to parse, and you will not know that you are missing that information. You can’t control, what you can’t see.
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis
This is the first in a series of blog posts that examine the topic of fully programmable data pipelines and their potential to transform the network visibility industry. Within this series we will be discussing what a programmable pipeline actually is, how solutions built with programmable pipelines differ from what has been available on the market, and the advantages organizations stand to gain by adopting such solutions.
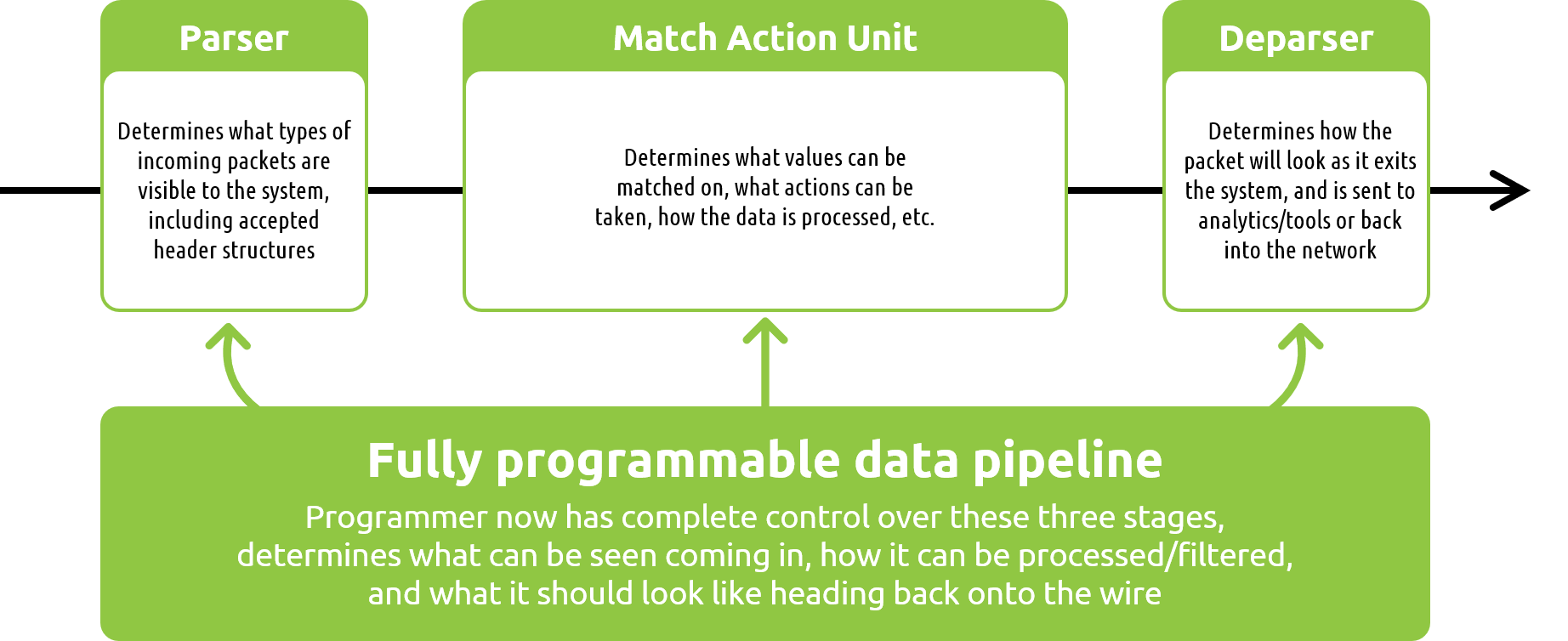
Before we begin, it is important to note that programmable pipelines are here today due to a key innovation made in the networking switch world- the development of a programmable ASIC/chip. This new chip, along with the open source language used to program the chip, have allowed a new breed of network visibility solutions to emerge. These solutions are dramatically different than legacy network packet brokers- solutions which are built using static, fixed-function ASICs.
Throughout this blog series we will make sure to cover the differences between these two solutions, as well as highlight the advanced visibility functions that are now available to users for the first time thanks to fully programmable data pipelines.
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis
DNS. A necessary mechanism that makes global network communications work, connecting services to the internet or private network, thereby powering our digital lives can also present confounding and problematic engineering challenges with cybersecurity implications. Site not responding, nefarious applications, applications not resolving, broken network connectivity…many initial responses are Is it DNS? it’s DNS, “It’s always DNS”.
DNS, the domain name system, connects domain names to IP addresses that locate and route information and traffic from a source location to a client can be the bane of many network and cybersecurity engineers as they maintain networks or investigate potential threats on the network.
We’ll look at this critical network component, its threat value and how you can make DNS an actionable component
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis,
cybersecurity
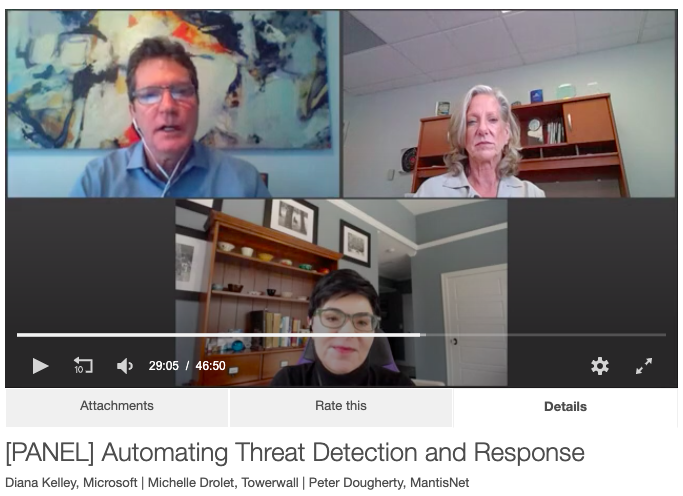
We had the pleasure of participating in a panel discussion with Michelle Drolet, CEO of Towerwall, Peter Dougherty, CEO of MantisNet and moderated by Diana Kelley, Cybersecurity Field CTO at Microsoft on automating threat detection and response.
Below you can read some of the highlights of the discussion and you can register (click the play button) to listen to the full discussion.
Read More
Tags:
cyber security,
Real-Time Monitoring,
mantis
In the beginning, networks and the Internet writ-large were designed with the notion of intrinsic security based on a perimeter wherein a person, application or third-party was verified and subsequently granted an all-inclusive ‘trusted’ status. Suffice to say, this approach has resulted in damages and incalculable losses on a global scale. Trust placed on verification at only of a few points of access has proven to be lacking. To put it mildly, according to the Cloud Security Alliance in their Software-Defined Perimeter Architecture Guide, “Today’s network security architectures, tools and platforms all fall short of meeting the challenges presented by our current security threats.” With recent (network) technology advances, we are now capable of building continuous verification to enable zero-trust.
Read More
Tags:
network engineering,
cyber security,
Real-Time Monitoring,
mantis
Digital transformation and the growing complexity of IT environments present new vulnerabilities that can be exploited by attackers for reconnaissance, delivering malicious payloads or to exfiltrate data. Using live network traffic for analysis to expose hidden malicious or anomalous activities and security threats among the complexity is fundamental for improved detection and response. So much so, that Gartner recently published an inaugural market guide for network traffic analysis (NTA), to help organizations understand what to look for (more on that later).
What is network traffic analysis (NTA)?
Network traffic analysis uses network communications and their protocols for detection, identification and analysis of cybersecurity threats and potential operational issues. As you’ll read, we propose doing this in real-time, with wire-speed network data and analytics to meet the demands of digital business and to gain an edge on reducing mean time to detect (MTTD) / mean time to respond (MTTR).
Read More
Tags:
cyber security,
Real-Time Monitoring,
mantis,
cybersecurity
As technologies advance and enterprise networks expand, administrators accountable for the overall health and performance of infrastructure accumulate more and more responsibility. CIOs are continually analyzing the problem of how to better monitor and secure the activity within their organization’s network.
Read More
Tags:
Real-Time Monitoring,
Data-at-Rest,
Data-In-Motion,
cybersecurity
MantisNet's recently published whitepaper, Solutions for the Next Generation of 5G and IoT Network Deployments, focuses on the enablement of real-time network intelligence, monitoring and analysis at the edge. This topic is very timely as telecommunications carriers are readying their fifth generation, or 5G, network deployments. The promise of higher speeds, lower latency and greater throughput has arrived to deliver improved digital experiences and further enable the continual growth of Internet of Things (IoT) connectivity and interactions.
Read More
Tags:
Real-Time Monitoring,
mantis
We had the pleasure of supporting the Software Engineering Institute at Carnegie Mellon University’s conference, FloCon: Using Data to Defend. The presentations and discussions at the event provided validation that changes are coming to network and cyber security. More mathematical solutions are being developed to fuel machine learning and algorithms to combat malicious and other network traffic of interest. If you missed the event, an overview and video of our presentation is below.
Read More
Tags:
network engineering,
Real-Time Monitoring,
DNS Monitoring,
Data-In-Motion,
mantis
MantisNet is a proud sponsor and participant at the upcoming FloCon 2019 conference in New Orleans, January 7-10, 2019.
We were excited to be accepted as a speaker and sponsor for the annual Software Engineering Institute at Carnegie Mellon University’s event. The theme for FloCon 2019 is ‘Using Data to Defend’ and the forum to “explore large-scale, next-generation data analytics in support of security operations” fits squarely within the core mission and vision of MantisNet.
Read More
Tags:
Real-Time Monitoring,
mantis