Solving the opacity problem - Bringing clarity to traffic obscured by encryption.
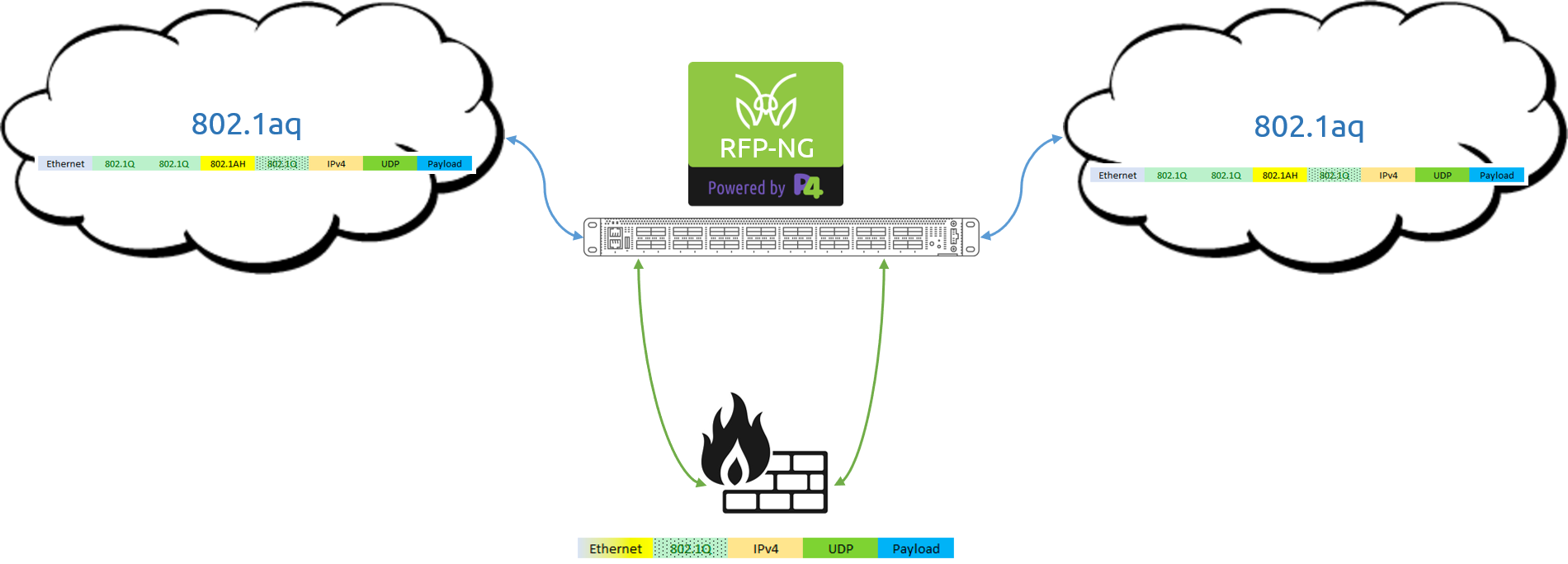
There are many reasons that the use of encryption will continue to increase as it provides a method of privacy and security of communications and lowers the risk of information loss. However, encrypted session traffic does pose a challenge in achieving visibility and observability of network events for day-to-day operational management, risk detection and response, and lawful intercept scenarios.
How can teams better leverage the information contained in encrypted network traffic sessions for real-time network visibility?
Read More
Tags:
Real-Time Monitoring,
Data-In-Motion,
mantis,
cybersecurity,
containers
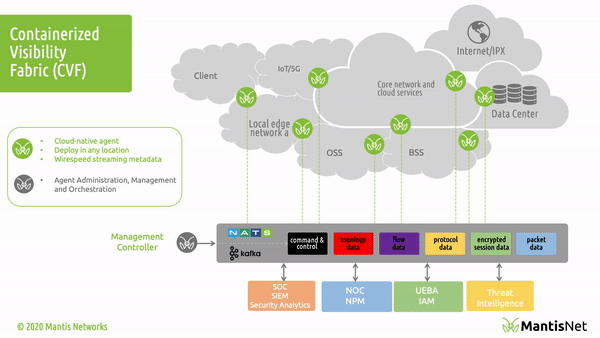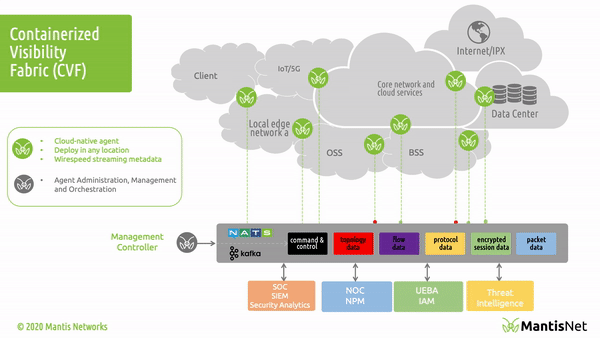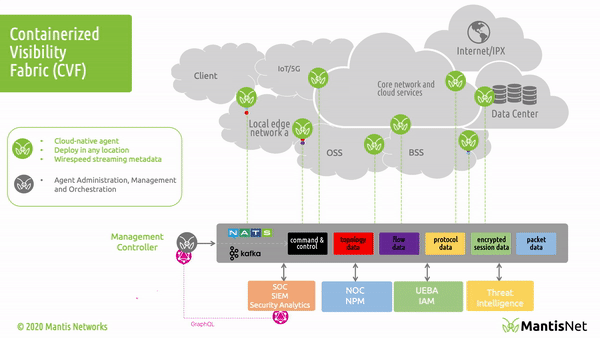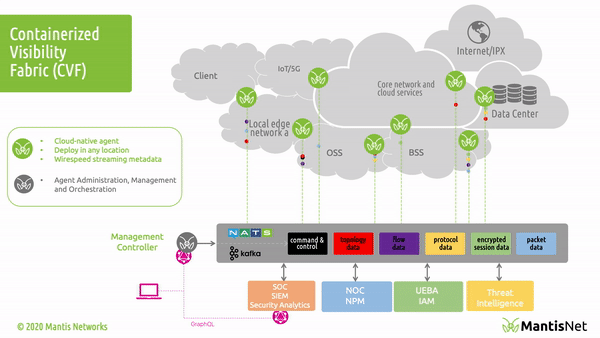
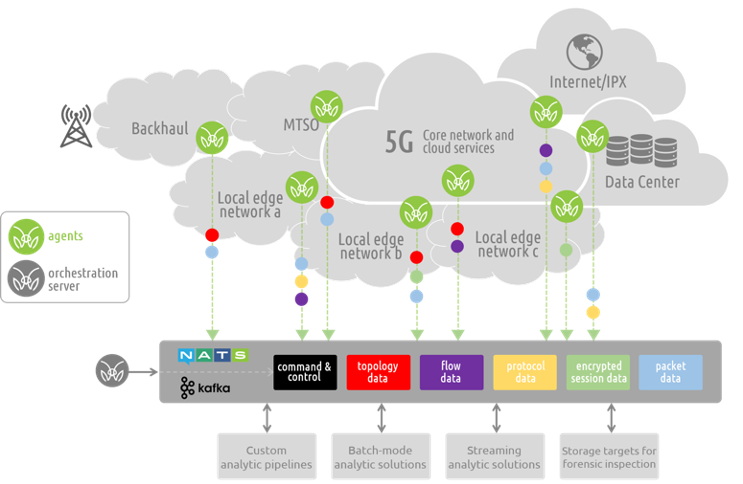
The MantisNet Containerized Visibility Fabric (CVF) is now generally available, and we want to provide a deeper dive into the challenges that we’ve seen with network visibility which compelled us to develop this much needed cloud native observability solution.
As we will discuss more deeply in this and future posts; serverless, cloud native systems are unique in that applications are deployed as microservices and containerized applications which can both more fully exploit the capabilities of the underlying machines and are further decoupled from the constraints of hypervisors. This provides programmatic visibility and access to the underlying nodes (hardware - machines) in such a way as to enable better scaling, fault isolation, observability and control.
In the cloud native world; network topology (physical and virtual) is hidden, interfaces (network namespaces) are hidden, data flows are hidden, and to make matters even more challenging - resources are dynamically configured, provisioned, deployed and reused.
Read More
Tags:
Real-Time Monitoring,
mantis,
containers,
cloud native network function
5G network architectures are redefining how resources are deployed, managed and utilized within a communications network. A fair blanket statement regarding these changes is that 5G is taking full advantage of cloud-native and virtualization technologies - even pushing them to the next level. These range from cutting edge, revolutionary 100% cloud native deployments from new entrants such as Rakuten, to the more measured non stand-alone (NSA) and hybrid architectures being deployed by the existing wireless service providers. One thing is clear- the days of capital-intensive dedicated physical infrastructure is meaning less and less as cloud-native technology is used to deploy dynamic, service-oriented, and highly scalable resources to deliver on the promises of 5G.
But, what does this mean for data visibility?
Read More
Tags:
network engineering,
network preformance,
Real-Time Monitoring,
mantis
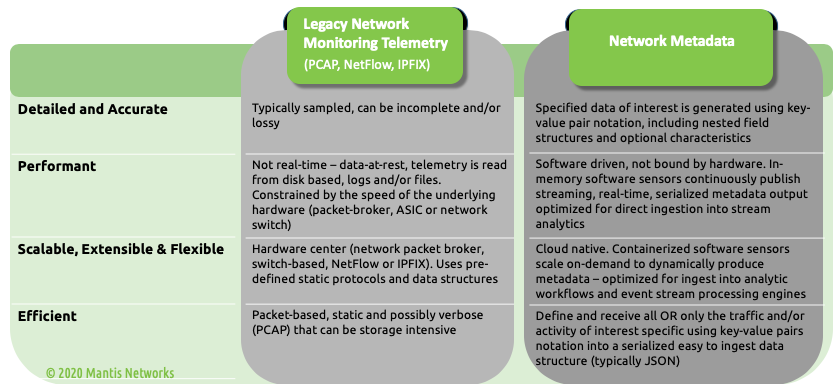
As we’ve shared previously - networks are the circulatory and nervous systems of your enterprise. Indeed; “the network is the computer”, and networks are an invaluable source of ground-truth. From a communications perspective, you can learn a lot by directly observing who is speaking, to whom they are speaking, the language they are using, the tone of voice, and the content of the communications. When it comes to network communications and metadata the analogies are obvious: in the case of DNS traffic- mapping URLs into IP addresses, and identifying underlying services and connected devices - in the case of TLS protocol, getting detailed insights into the encryption capabilities and device characteristics - likewise the GTP protocol provides geo-location specific information, and in the case of the MODBUS protocol, understanding the communications within industrial control systems.
Read More
Tags:
Real-Time Monitoring,
Data-In-Motion,
mantis,
cybersecurity
Announcing the MantisNet Network Stream ProcessorSM App for Splunk
We’re excited and proud to announce that the MantisNet Network Stream ProcessorSM (NSP) App for Splunk is now available.
The App enables ingestion of streaming network metadata using key-value pairs: a powerful, new form of serialized metadata produced by MantisNet sensors. Customers can now access, integrate and manage these new forms of lossless, ultra-efficient, ultra-accurate and high-resolution metadata, to support continuous real-time network detection and response in Splunk.
Read More
Tags:
Real-Time Monitoring,
DNS Monitoring,
Data-In-Motion,
mantis,
cybersecurity
This is a continuation of our blog series on the advanced functions for network visibility solutions with fully programmable data pipelines. Read our introduction to the series here.
Another great example of the power behind fully programmable pipelines is the ability to gain insight into the actual visibility solution itself. Solutions such as the MantisNet RFP-NG are able to leverage the processing logic of these pipelines to better visualize what types of events are unfolding on the wire over time and provide metrics related to the rules that are running. Once again, let’s simplify things here for a moment to best understand this concept….
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis
This is a continuation of our blog series on the advanced functions for network visibility solutions with fully programmable data pipelines. Read our introduction to the series here.
The biggest elephant in the network visibility room has always been the fact that you don’t know what you are missing. If there are packets with structures that fall outside of your fixed-function ASIC-based chip/solutions capabilities (and trust me, there always are), you are not only going to drop those packets, but you also have zero indication that you just missed a packet. The packets simply fail to parse, and you will not know that you are missing that information. You can’t control, what you can’t see.
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis
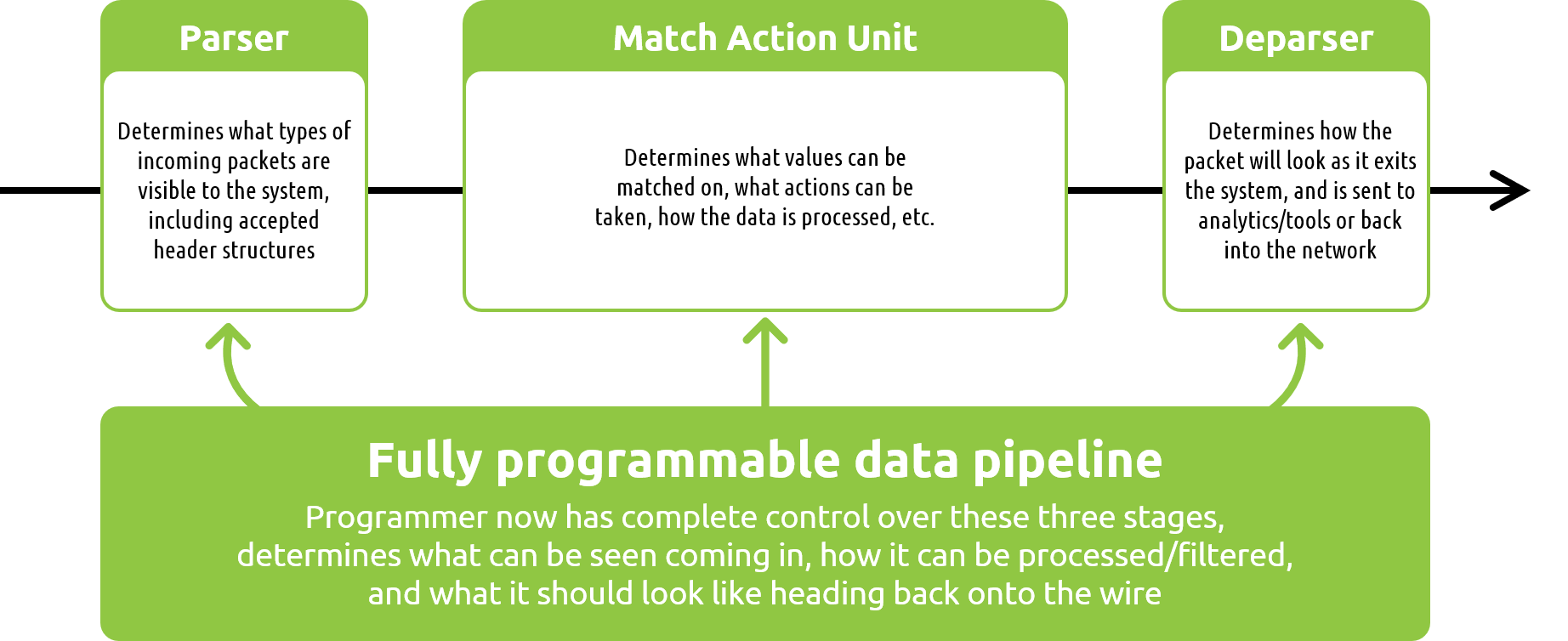
This is the first in a series of blog posts that examine the topic of fully programmable data pipelines and their potential to transform the network visibility industry. Within this series we will be discussing what a programmable pipeline actually is, how solutions built with programmable pipelines differ from what has been available on the market, and the advantages organizations stand to gain by adopting such solutions.
Before we begin, it is important to note that programmable pipelines are here today due to a key innovation made in the networking switch world- the development of a programmable ASIC/chip. This new chip, along with the open source language used to program the chip, have allowed a new breed of network visibility solutions to emerge. These solutions are dramatically different than legacy network packet brokers- solutions which are built using static, fixed-function ASICs.
Throughout this blog series we will make sure to cover the differences between these two solutions, as well as highlight the advanced visibility functions that are now available to users for the first time thanks to fully programmable data pipelines.
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis
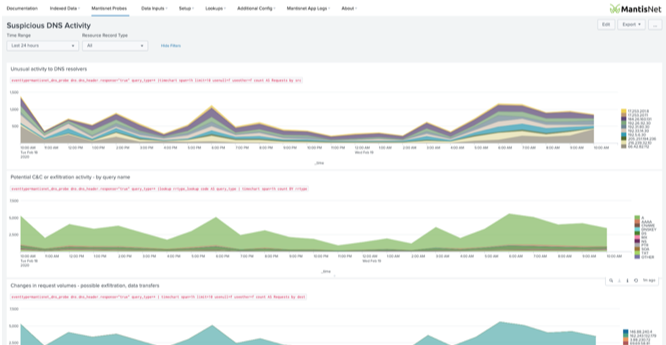
DNS. A necessary mechanism that makes global network communications work, connecting services to the internet or private network, thereby powering our digital lives can also present confounding and problematic engineering challenges with cybersecurity implications. Site not responding, nefarious applications, applications not resolving, broken network connectivity…many initial responses are Is it DNS? it’s DNS, “It’s always DNS”.
DNS, the domain name system, connects domain names to IP addresses that locate and route information and traffic from a source location to a client can be the bane of many network and cybersecurity engineers as they maintain networks or investigate potential threats on the network.
We’ll look at this critical network component, its threat value and how you can make DNS an actionable component
Read More
Tags:
network preformance,
cyber security,
IT operations,
Real-Time Monitoring,
DNS Monitoring,
mantis,
cybersecurity
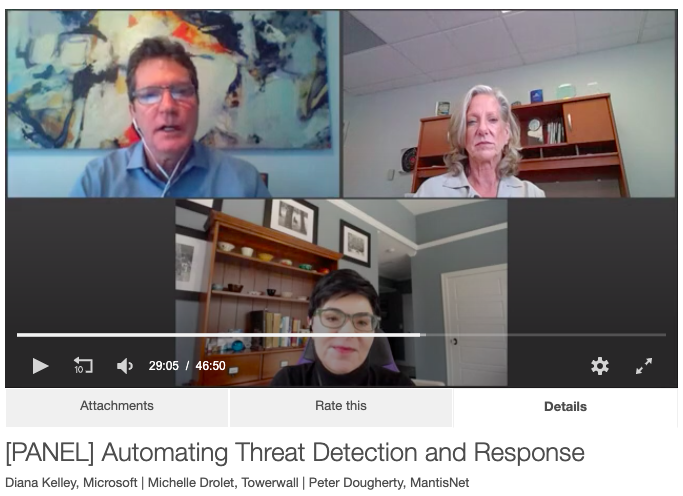
We had the pleasure of participating in a panel discussion with Michelle Drolet, CEO of Towerwall, Peter Dougherty, CEO of MantisNet and moderated by Diana Kelley, Cybersecurity Field CTO at Microsoft on automating threat detection and response.
Below you can read some of the highlights of the discussion and you can register (click the play button) to listen to the full discussion.
Read More
Tags:
cyber security,
Real-Time Monitoring,
mantis